Protect Industrial IoT Infrastructure with Converged IT/OT Security Gateways
Industrial and other mission-critical facilities and processes are increasingly being connected and digitized to provide greater process insights and improve efficiency and safety. But traditional operational technology (OT) infrastructure such as programmable logic controllers (PLCs), remote terminal units (RTUs), and supervisory control and data acquisition (SCADA) systems were not designed to defend against the types of sophisticated hackers and malware attacks that target devices connected to the Internet.
Security vulnerabilities in OT environments are exacerbated by the IT conundrum described by Max Lee, Chief Technology Officer at Lanner Electronics Inc.: “Traditional IT security, mainly built around enterprise network needs, is designed in the server room to mitigate the cyber threat from the Internet. It’s not developed to protect the industrial control system (ICS) and SCADA networks.” That’s because OT devices function in segregated environments to control and monitor critical infrastructures.
To improve security, Lee said, "We need to have industrial-grade firewalls deployed in harsh industrial environments where PLCs, RTUs, and other devices are located." In addition, features such as surge protection, LAN/COM isolation, and wide operating temperature range also help ensure that a firewall can efficiently work 24/7 in rugged industrial conditions.
Therefore, a mutual understanding of both IT and OT domain requirements must be considered when implementing secure Industrial Internet of Things (IIoT) network architectures.
Standardizing Security Is a Good Start
The idea of getting systems to communicate before implementing security is a precursor for the IIoT. As important as it is for OT owners, designers, and developers to give more consideration to security firewalls, they cannot do so in a vacuum. OT systems must also connect to IT infrastructure to make use of the data. For instance, employees in central locations must be able to remotely connect to the OT network to access data and monitor status via the company's enterprise PCs.
At the same time, serial ports, which are not available in typical IT firewalls, are also required to connect to legacy devices in industrial networks. These myriad connections with unreliable security create loopholes for the introduction of malware and viruses into IT offices and industrial networks.
In the energy sector, some of these challenges have already been tackled. The IEC-61850 specification ensures interoperable communications among automation systems, and is required for industrial firewalls. In a similar fashion, a rise in the number of cyber attacks on critical infrastructure devices has led to the creation of other new security frameworks for industrial systems. Network hardware vendors like Lanner Electronics are developing security appliances based on the Critical Infrastructure Protection (CIP) standards spearheaded by the North American Electric Reliability Corporation (NERC) in the form of IT and OT gateways that act as multilayer network security platforms.
The NERC CIP standards help bring IT and OT together seamlessly by specifically addressing the security policy management and control-network visibility requirements of converged IT and OT infrastructure (Figure 1). Using CIP standards, gateway devices can integrate technologies from both domains to establish visibility into control network traffic as well as whitelisting, packet inspection, and security policy instructions at ICS and SCADA sites. Lanner has already taken this approach with its LEC-6032 converged IT/OT security gateways aimed at industrial markets such as energy, oil and gas, and manufacturing.
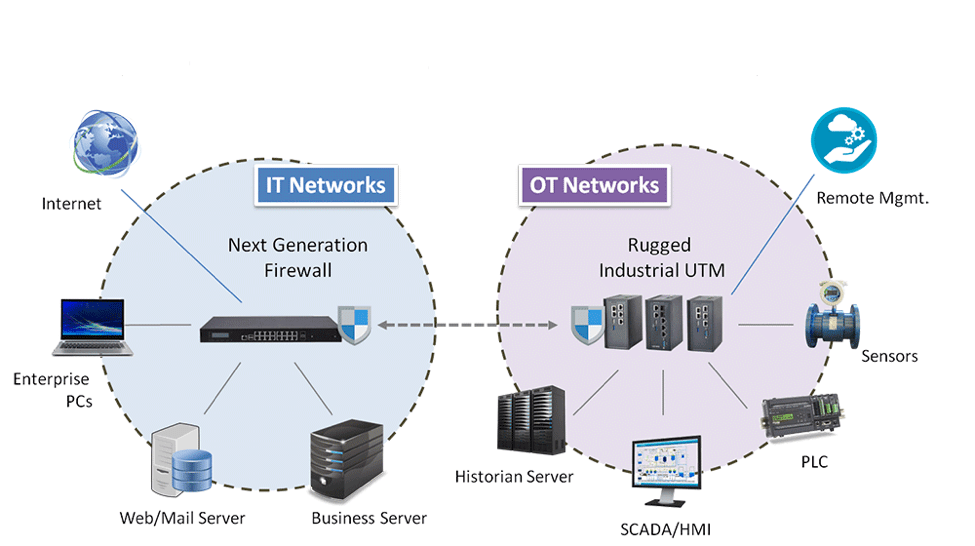
Anatomy of an IT/OT Security Gateway
What Lanner’s security gateway offers is an ambidextrous approach for protecting OT devices on one side and IT networks on the other through off-the-shelf technology building blocks based on CIP standards. On the OT side, these gateways deploy a security appliance to integrate SCADA, PLCs, and log servers. For the IT environment, the CIP gateways protect the enterprise resource planning (ERP), product lifecycle management (PLM), and mail servers.
For example, Lanner's LEC-6032 industrial-grade fanless embedded system acts as an industrial firewall and unified threat-management (UTM) device to monitor and control the network traffic in OT environments. The LEC-6032's firewall solution for OT security is driven by an Intel Atom® E3845 processor running at 1.91 GHz. This low-power processor has performance that's steady enough for network traffic management. “Atom’s low power consumption enables the wide operating temperature range, which is critical in the OT network,” said Lanner’s CTO Lee; but the system also leverages the Atom processor's security features.
The Atom CPU comes with virtualization functions, an Execute Disable Bit feature to reinforce system security and network defense, and Advanced Encryption Standard – New Instruction (AES-NI) technology (Figure 2). Furthermore, the CPU is scalable for instruction and policy implementation to detect unauthorized behaviors and malware. In addition, it can conduct validation and authentication processes to establish the identity of each device in the OT infrastructure.
Likewise, Lanner uses the Intel® Core™ processor in its IT firewall security appliances. Here, Lee quoted the processor’s high-throughput processing capability for implementing security instructions such as deep packet inspection (DPI) and the Data Plane Development Kit (DPDK). Intel® QuickAssist technology is also used in Lanner’s IT security appliances for crypto acceleration. The security gateway hardware is based on the x86 architecture, which enables porting of any software compliant with the architecture.
MultiLayer Security
According to research data from Lanner, more than 60 percent of utility companies have encountered at least one security breach in the past year. The nature of OT infrastructure and the number of attack points it offers hackers with malicious intentions demand a multilayer network security platform. This is especially true when IT elements are intertwined with OT.
CIP-based security gateways offer risk analysis, network monitoring, and contingency against cyber-attacks on critical industrial infrastructure.