Zero-Touch Provisioning for 5G Networks

One of the physical changes in 5G is that base stations need to be much closer together—often only a few hundred meters apart. This is because 5G uses shorter but more powerful wavelengths than its predecessors.
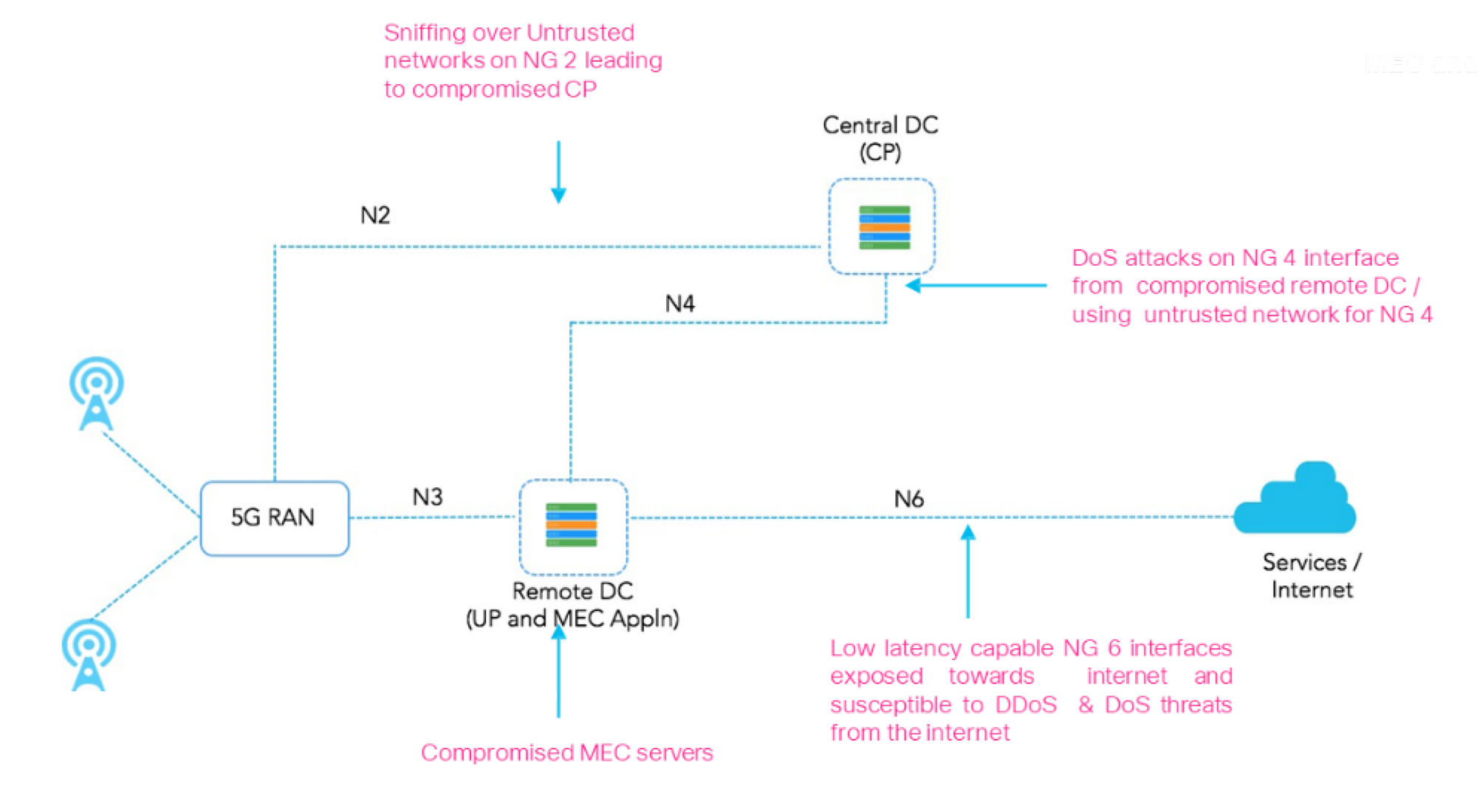
The increase in base stations—and corresponding growth in network nodes—means that the number of potential security vulnerabilities and attack surfaces will expand significantly (Figure 1).
Authentication Shores Up Potential Security Issues
One way to shore up security in 5G networks is with more robust device authentication. This technology isn’t new, but it requires some changes in 5G.
All authentication deals with three segments of the network infrastructure:
- The equipment requesting information
- The network that carries the request
- The endpoint where the request terminates
Procedures like public key exchanges use these network elements to verify that each party involved in a communication is who it says it is. 5G networks are similar, except the network elements are:
- The equipment requesting information
- The network that carries the request
- An endpoint network (or local network) where that request terminates
The distinction here is that the requesting information must first authenticate with an edge network before reaching the endpoint itself (Figure 2). This approach, known as Primary Authentication, mitigates the risks that can occur if a bad actor somehow makes its way onto the network. For example, it protects against side-channel attacks that could otherwise compromise dozens of devices.
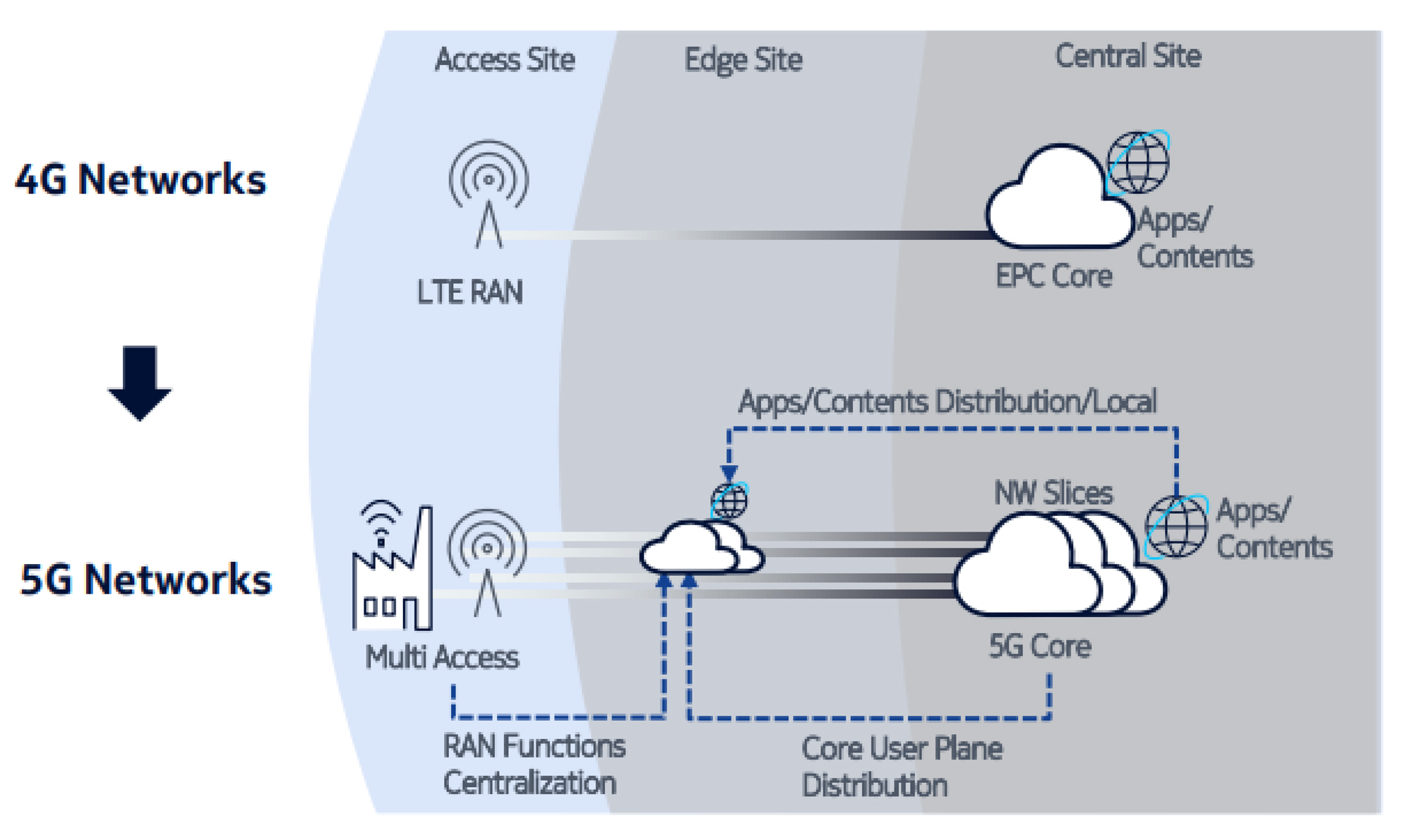
To achieve this, a secure function that operates between the source and destination networks allows the authenticating network to reject any authentication request. The endpoint network itself has final authority on whether to authenticate or deny incoming requests. This is mandatory for all 5G networks.
So during the Primary Authentication process, a cryptographic key is generally shared with the authentication server on the endpoint network, where the keys are stored. Requests are then sent back and forth over the network to ensure that security is maintained using those shared keys, just like your standard PKI.
One way to shore up 5G network security is with more robust device authentication. This technology isn’t new, but it requires some changes in 5G. @telit
Protecting Network Nodes
Of course, all authentication is based on the ability to trust the identity of devices on a network. This means each endpoint must be secured, which is the responsibility of IoT and other connected device OEMs.
Maintaining the integrity of these device identities requires a combination of hardware security and comprehensive device management.
Take Telit OneEdge for example. This IoT device management Platform-as-a-Service (PaaS) works with the company’s 5G-enabled cellular modules. At the time of manufacture, the modules supported are pre-provisioned with a unique ID, device credentials, and SIM functions locked away in a trusted region of the hardware.
Corresponding credentials for each module are stored in a secure cloud environment, allowing devices to authenticate with the OneEdge platform as soon as they join a network. This process—known as zero-touch provisioning—ensures that device identities can be trusted from the instant they attempt to register (Figure 3).
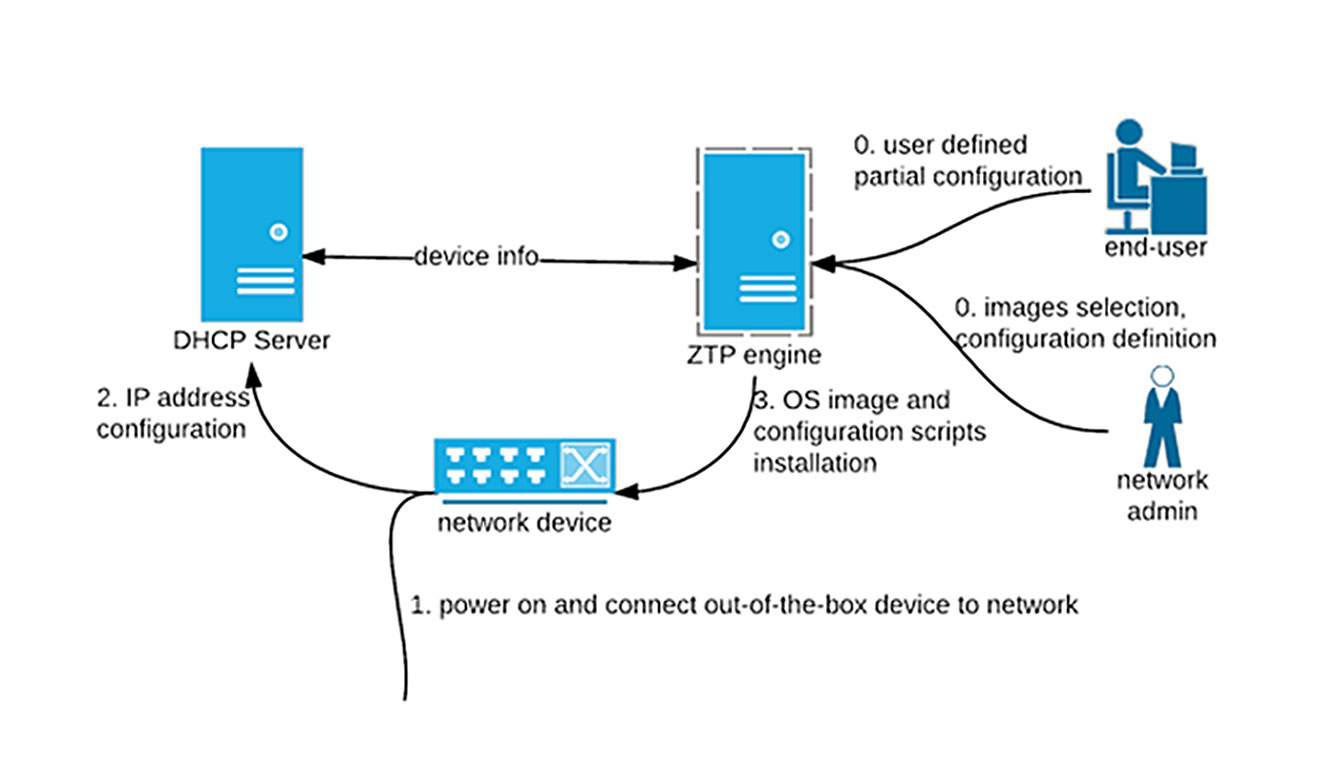
Once connected, OneEdge users can seamlessly monitor devices from a cloud-based dashboard. This dashboard supports automated action, alerts, and alarms that can be used to identify and prevent suspicious network activity (Figure 4). It also integrates device management and over-the-air update functionality via the Telit AppCenter so that device OEMs can quickly resolve vulnerabilities.
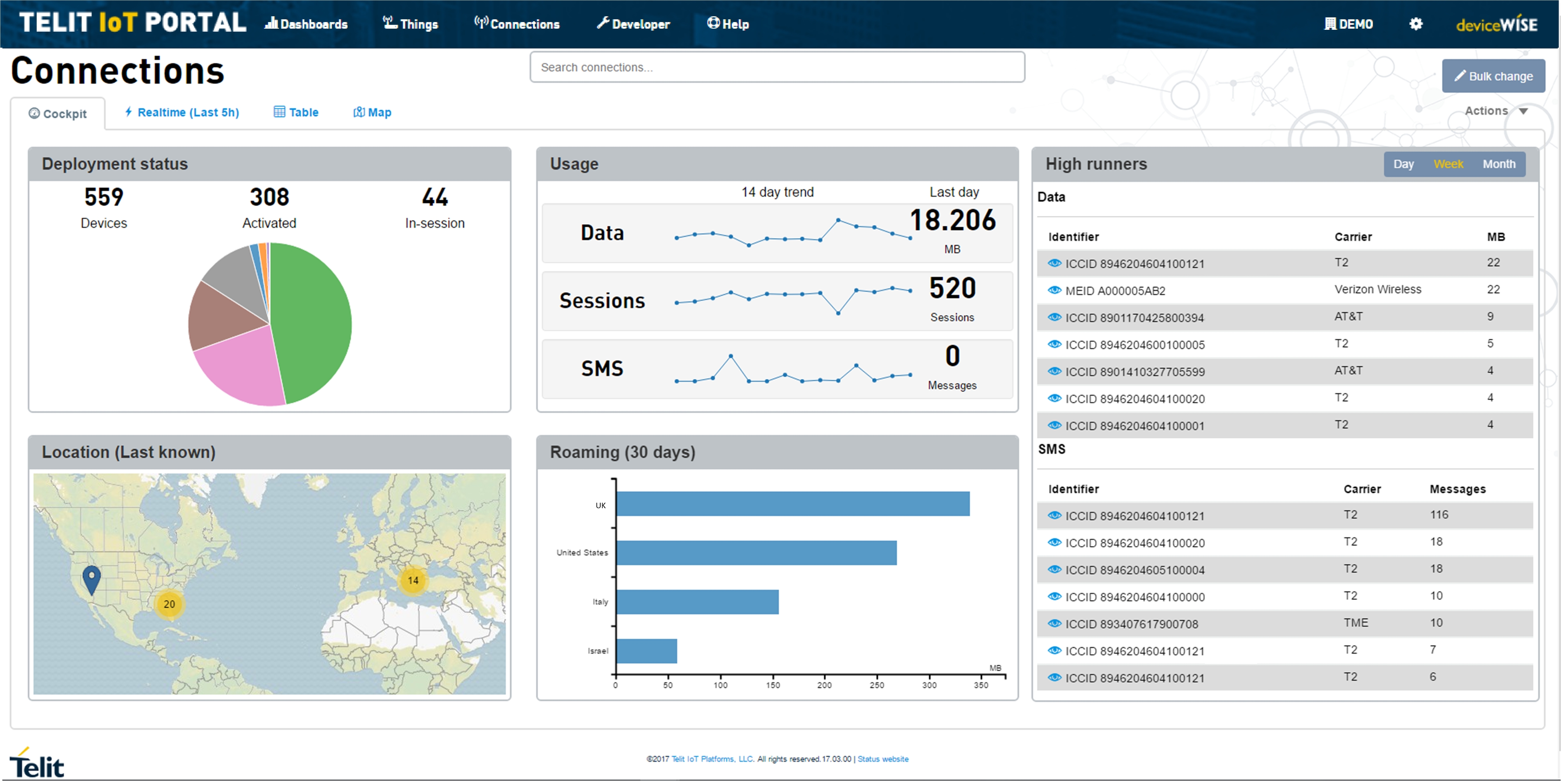
Telit OneEdge is compatible with a wide range of carrier networks, including Verizon, AT&T, Vodafone, T-Mobile, and Telefonica. Cloud connectors also provide secure integration with other enterprise IoT platforms such as AWS, Google Cloud, Microsoft Azure, IBM Watson, SAP, MindSphere, and the Oracle Cloud.
Beyond 5G
Primary Authentication provides a new layer of protection for 5G networks. But Primary Authentication is not a cure-all. Preventing sniffing, man-in-the-middle, denial-of-service (DoS), side-channel, and other network attacks starts with trusted identities in each network endpoint.
As more and more IoT devices come online thanks to 5G technologies like NB-IoT and LTE Cat-M, securing our networks will require collaborative efforts among mobile network operators (MNOs), network equipment providers (NEPs), and connected device manufacturers.
Primary Authentication, zero-touch provisioning, and trusted hardware provide a defense-in-depth security strategy for 5G IoT networks. To protect data, devices, and brand reputations, everyone must play their part.