Securing the Autonomous Car
Connected and automated automobiles are becoming a major market and platform for third-party hardware and software. Some estimates say the market could grow to $155 billion by 2022.
But security is proving a problem. In 2015, hackers demonstrated they could take control of a car traveling 70 miles per hour. In March 2016, the FBI issued a public service announcement warning that vehicles are increasingly vulnerable to remote exploits over the Internet.
Once in, attackers can interfere with almost any system in a car through various electronic control units. These units control steering, braking, acceleration, and other critical functions such as keyless entry, airbags, and wireless connectivity. With up to 100 electronic control units in a modern car, there is significant vulnerability whether a vehicle is parked or moving.
To get engineers, designers, companies, and consumers to fully embrace the autonomous car will require a dedication to systems built on a secure hardware and software foundation. Security features will need to include:
- Hardware based root-of-trust, e.g., secure boot, OS authentication, encryption, and management of cryptographic keys and signatures generated during manufacturing
- Real-time priority processing for critical safety functions
- Continuous monitoring of automotive software and hardware processes
Implementing these features will require a layered defense in depth approach (see Figure 1). The more layers of protection, the more difficult for an attacker to break through.
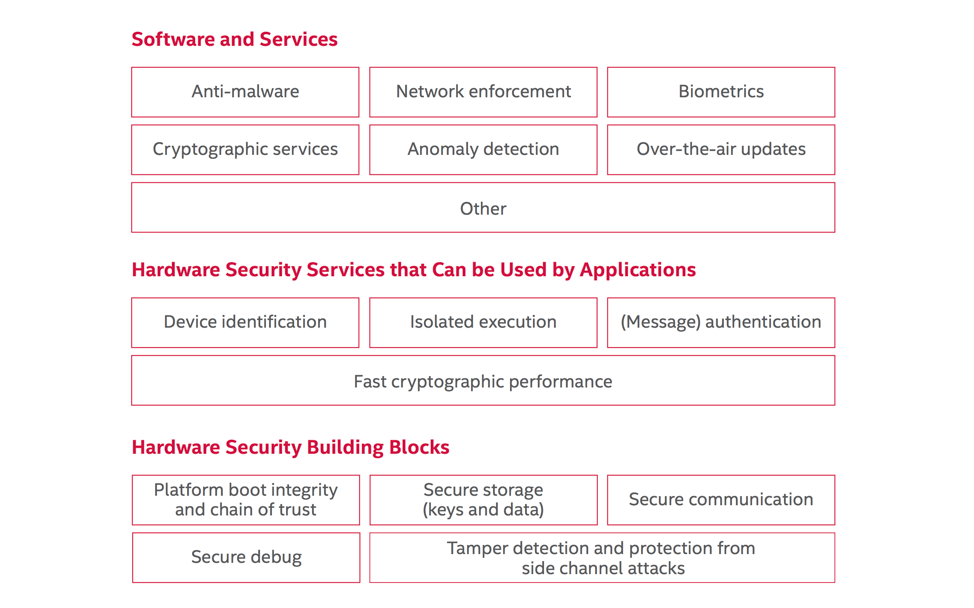
A Processor Designed for Automotive Security
One essential component in a secure hardware foundation is an automotive-grade SoC designed with built-in security features like the new Intel Atom® processor A3900 series. These processors include a converged security engine with a dedicated security coprocessor that adapts security to the critical nature of each function. The processors also offer secure boot, fast cryptographic execution, and secure storage for key exchange and encryption to ensure only authorized over-the-air updates can happen. A new Intel® Trusted Execution Engine (Intel® TXE) helps protect data even if the OS is compromised.
Specifically developed for next-generation in-vehicle infotainment (IVI) experiences, the Intel Atom processor A3900 series enables a software-defined cockpit solution that further enhances security through the consolidation of IVI, digital instrument clusters, and advanced driver assistance systems (ADAS) features (see Figure 2). By supporting a platform that can handle more independent systems, parts, and interconnections, these processors minimize the vulnerable points in a vehicle, and reduce overall design and manufacturing complexity.
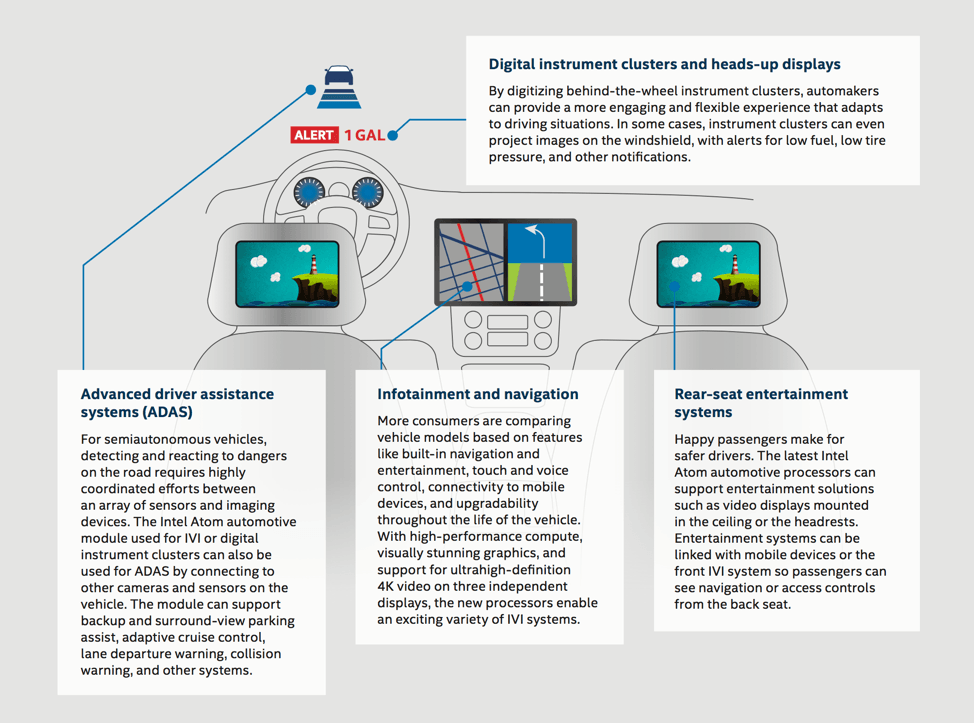
The Intel automotive portfolio has security as a fundamental foundation. Starting with the current advanced in-vehicle experiences made possible by the Intel Atom processor A3900 series, followed by next-generation SoCs to complement the spectrum all the way up to fully automated driving of tomorrow.
Secure Automotive Software
Secure software is also vital for protecting automotive systems. In the following sections, we highlight some of the options available for systems based on the Intel Atom processor A3900 series. These include:
- Wind River Helix* Chassis
- Green Hills Platform for Automotive
- BlackBerry QNX
Each option provides a comprehensive platform for advanced automotive designs, built on a solid foundation of security.
An OS for the Chassis
A good example can be seen in the Wind River Helix* Chassis suite of automotive software offerings (Figure 3). Wind River Helix* Chassis provides the framework for connectivity, security, and flexibility to integrate systems within vehicles—and external devices and data outside the car.
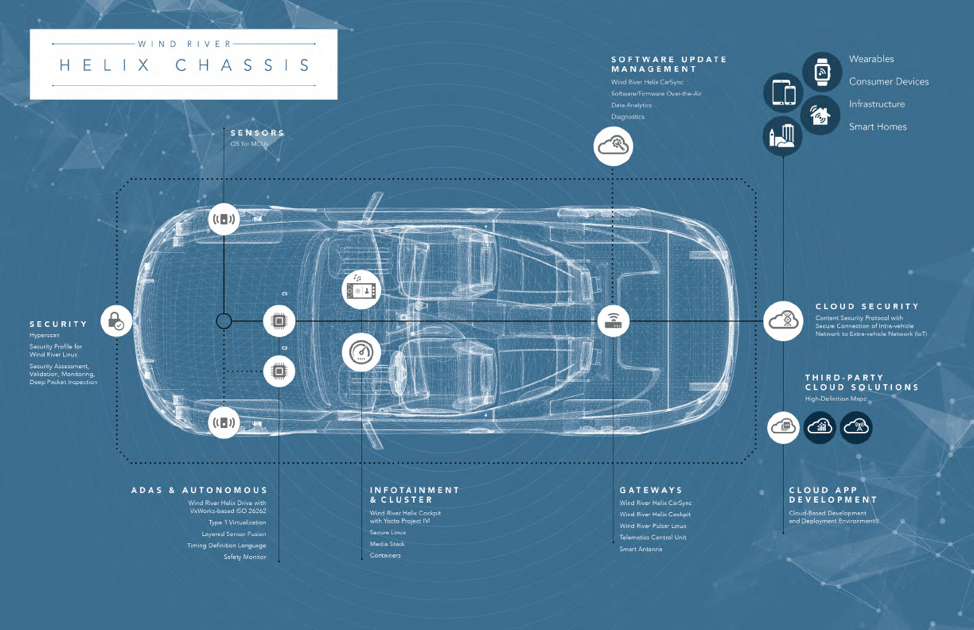
This comprehensive framework of software solutions spans the full range of technologies for the connected car, such as:
- Infotainment, telematics, and digital cluster systems
- Safety-oriented systems such as advanced driver assist systems (ADAS) and autonomous driving systems
- Over-the-air (OTA) update technologies
- Cloud-based development tools
Key to enabling the safety and security for automated driving is Wind River Helix Drive. Based on Wind River's VxWorks* real-time operating system (RTOS), Helix Drive delivers the deterministic performance and low latency required for developing safety-critical, ISO 26262-certifiable automotive applications.
Wind River's platform can also create robust partitions within one or multiple OSs on a single- or multi-core processor. Having the kernel separated from applications, protocols, and other packages enables greater security. In addition, separation enables OSs of mixed levels of criticality to be consolidated on the same processor without complete re-certification. Knowing that already-tested functions will not be impacted by new, non-overlapping features also makes software integration more predictable and robust.
Other modules contribute to overall security at the system level. For instance, Helix CarSync adds an OTA solution for remotely managing and maintaining system integrity. Helix CarSync can also collect critical data across the entire lifecycle of the vehicle, from preproduction to the final mile.
Another example is Helix Cockpit, a Linux-based software platform for IVI, telematics, and automotive instrument cluster systems. Helix Cockpit provides additional security enablement within the car and in cloud environments as well.
Additionally, drawing from its heritage in mission-critical industries and championing a multi-tiered security approach, Wind River can assist at each step to secure an entire automotive system, from initial design to development and lifecycle maintenance, and help carmakers deliver secure and safe vehicles.
Proven Safety and Security
Green Hills Platform for Automotive is another strong option (Figure 4). This platform builds on decades of automotive experience to create a secure, safe foundation for advanced automotive software.
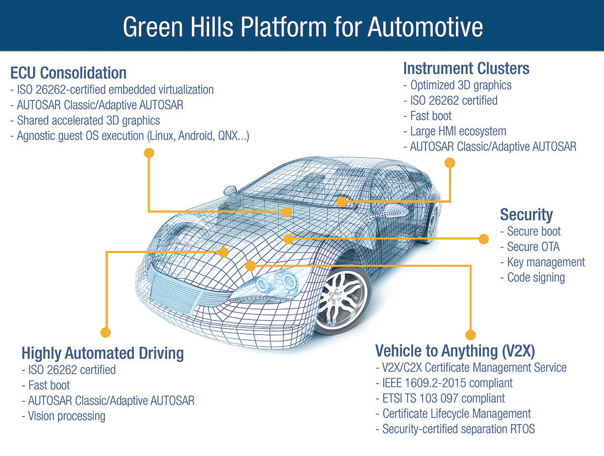
Solutions available in this Green Hills platform span all automotive electronic subsystems, including:
- ECU consolidation
- Instrument clusters
- Secure gateway
- Security/authentication/OTA
- V2X with certificate management
- ADAS
Based on the safety- and security-certified INTEGRITY separation kernel, this platform can consolidate workloads of different levels of criticality/certification on the same single- or multi-core processor. This capability is enabled by Green Hills' INTEGRITY Multivisor, which can run unmodified guest OSs in secure partitions alongside native real-time tasks (see Figure 5).
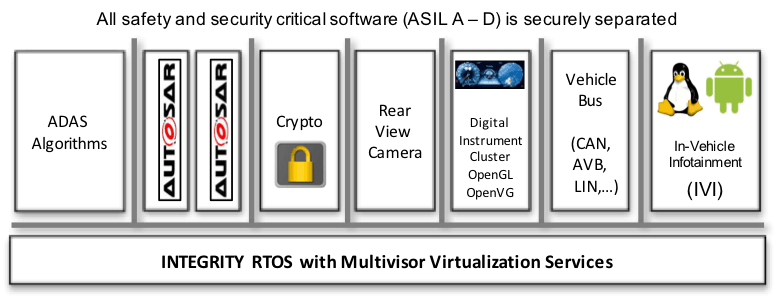
This proven architecture helps ensure that any safety or security flaws in one partition do not affect applications running in other partitions. It also provides a platform for the safe, secure consolidation of software from a range of sources—e.g., OEM, Tier1, and 3rd-party suppliers.
INTEGRITY’s built-in memory protection, microkernel architecture, and virtual device drivers ensure that the kernel is unaffected by bugs in application code. That's a good thing, as bugs are inevitable in a sophisticated IVI system.
In addition to memory protection, INTEGRITY guarantees that each application gets the memory and CPU resources it needs. Thus, a memory leak in a lower-criticality virtual address space cannot affect the operation of the higher-criticality virtual address space.
The same partitioning and resource guarantees protect applications from Internet-borne worms or viruses. If a virus got into the system via the IVI environment, for example, other independent applications in the system could not be attacked or starved of memory or CPU time. Similarly, a bug or design flaw in a less critical component cannot adversely affect another independent component.
Green Hills offers additional support through its INTEGRITY Security Services division, including:
- V2X/C2X certificate management services that are IEEE 1609.2-2015 and ETSI TS 103 097 compliant
- End-to-end certification life cycle management
- On-board electronic secure boot services
- Secure OTA and key management/code signing
- Cryptographic toolkits certified by the Federal Information Processing Standards (FIPS) for vehicle-to-everything (V2X) communications
With complete support for the Intel Atom® processor A3900 series, the seamless integration of Green Hills Platform enables carmakers and their suppliers to significantly reduce development cost and time to market while building the safest and most secure vehicle electronics.
A software platform for the vehicle
Developers can also choose the market leader in automotive software: BlackBerry QNX. The BlackBerry QNX software can be found in 240+ vehicle models and more than 60 million cars today. BlackBerry QNX offers platforms for the whole car – instrument cluster, infotainment, telematics, V2X, acoustics, control gateways, domains controllers, functional safety, and ADAS (). Security is built in and managed from the chip to the OS to every level of software, from the car to the cloud.
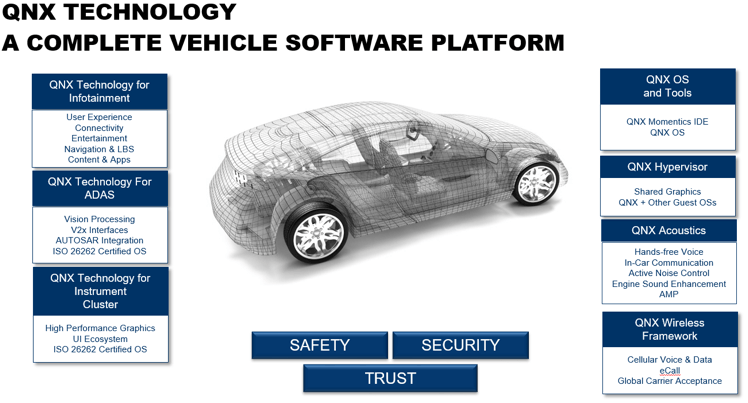
The foundation for all these platforms is the QNX Neutrino RTOS – a reliable and secure microkernel OS with industry-leading security. Both the OS and its tool chain are certified to ISO 26262 ASIL D, IEC 61508 SIL 3, and IEC 62304 for use in any safety-critical automotive system.
Modern domain controllers using powerful CPUs such as the Intel Atom A3900 processor need virtualization to isolate domains and functions, each running a dedicated OS. This virtualization is necessary to ensure that one guest OS cannot corrupt another OS. Plus, virtualization offers another level of security between OSs.
To deliver these advanced features, BlackBerry QNX offers a true Type 1 Hypervisor. This hypervisor is optimized for Intel processors for maximum performance and security.
BlackBerry's QNX software and security are enhanced by Blackberry Certicom. This service:
- Protects chips via keys injected during manufacturing
- Encrypts file systems with FIPs 140-2 protection
- Manages PKI certificates for authentication and authorization
- Provides secure over-the-air software update management
- Offers services such as vulnerability and penetration testing
BlackBerry technologies can help you in securing a complete, end-to-end solution for autonomous drive—from the vehicle to the cloud—with faster time to market.
Giving New Meaning to "Safe Driving"
Automotive cybersecurity is a challenge, and a responsibility, for the entire automotive ecosystem. No single company or technology will be able to solve the challenges alone.
To achieve increased awareness and adoption of security architectures for connected and automated vehicles, Intel partnered with Aeris and Uber to form an industry consortium. Once known as the Automotive Security Review Board, this consortium was recently relaunched with an expanded mission known as FASTR (Future of Automotive Security Technology Research).
FASTR provides a neutral, pre-competitive, open environment through which the evolving automotive ecosystem can collaborate. FASTR brings together auto-industry veterans and disruptors, technology giants and startups, leading academics and hackers.
These collaborators create agile, iterative research and produce reference architectures, proofs of concept, code samples, white papers, best-known methods, and more. The end result is innovation that automotive original equipment manufacturers (OEMs) need to drive requirements across their supply chains, reduce risks and liabilities, and foster trust in connected and autonomous vehicles of the future.
FASTR seeks to collaborate with complementary, like-minded organizations in this effort. To learn more, visit fastr.org or connect@FASTR.org.
Driving Consumer Acceptance
As carmakers add autonomous driving and connected vehicle features, establishing their safety will be paramount to ensuring their acceptance. With the help of companies like Wind River, Green Hills, and QNX, manufacturers and third parties can incorporate layered security throughout their automotive systems.
By delivering the next age of driving experiences safely and profitably, companies on the forefront of automotive technology can secure their place in this new world.