Beyond Bitcoin: How Blockchains Secure the IoT
IoT security is a thorny problem. It's not enough to secure individual devices. Developers must also protect the connections their devices will make with embedded and IT systems already in the field.
Blockchains are a powerful way to protect these connections, but this technology is difficult to implement within legacy systems. To work around this problem, companies like SPARKL have created solutions that allow new, blockchain-enabled devices to interoperate with existing equipment for end-to-end security—even if the network contains untrusted devices.
The IoT Security Challenge
Many embedded and IoT products are deployed in markets where size, weight, and compute performance are all at a premium—and where many aspects of the network are out of the end customer's control. In this context, traditional IT security approaches like localized antivirus software or hardened network infrastructure are impractical.
For these markets, security must be built into IoT devices and protocols, not provided by aftermarket software. That's where blockchains come in.
Bitcoins and Blockchains
If you’ve heard of blockchains, it’s probably in relation to Bitcoin—the digital cryptocurrency that relies on a blockchain to maintain a record of previous transactions.
The term blockchain is used in both a narrow and a wide sense. Construed narrowly, it refers to the specific implementation Bitcoin uses to create, maintain, and secure its own transaction record.
More broadly, it refers to the use of distributed ledgers to secure and maintain transaction ledgers that are equally accessible to any stakeholder or authorized individual. Sometimes the phrase “mutual distributed ledger” (MDL) is used interchangeably with blockchain, but the two terms are not identical. Every blockchain is a mutual distributed ledger, which is to say, every blockchain is an independent, transparent, permanent database capable of existing in multiple locations simultaneously, but not all MDLs are blockchains.
At the simplest level, a blockchain is a persistent ledger of transactions. Each group of transactions (called blocks) is cryptographically secured and its links to previous transactions are validated.
Think about a succession of blocks, each linked to the previous, and the “blockchain” moniker becomes clear: It’s a literal description of how transaction records are stored and authenticated, with timestamp information and record data cryptographically hashed into every block. Because the hash of each new block is partly based on the hash of all the blocks before it, there’s no way to edit or alter a blockchain without the tampering becoming immediately apparent, and changes to the record (if they are permitted at all) are permitted only if a majority of participants agree to them.
Early Signs of Success
Intel®, which announced its own blockchain platform a year ago, has already built demonstrations of how blockchains and the IoT can be used to track seafood as it moves through the supply chain (Figure 1).
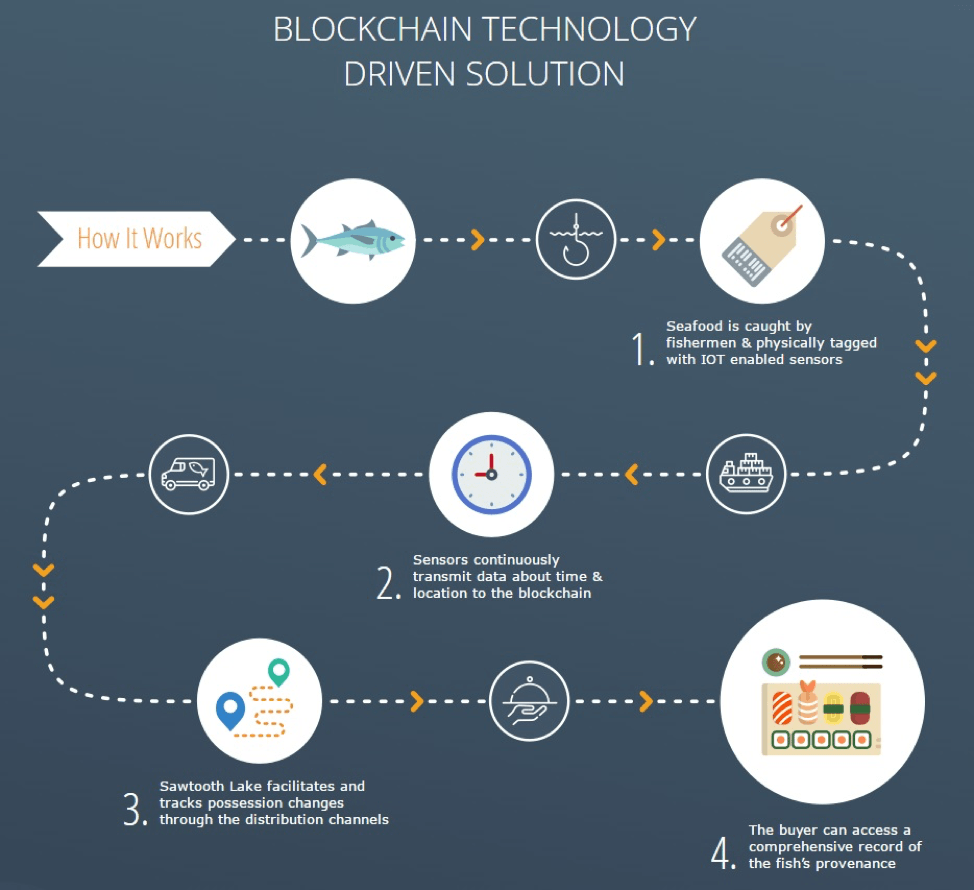
By monitoring products as they move through its distribution network, a supplier or buyer has dramatically increased its ability to quickly and definitively locate the source of any contaminated food, or to identify who had custody of a product at any given point in time. In case of a product recall or contamination problem, blockchain-based ledgers would allow a company to identify which products were sold from which stores, and would reach out to customers who purchased them.
Blockchain technology is also being evaluated as a method of securing IoT devices by assigning physical products a unique identity to ensure the authenticity of each specific device. Currently, IoT devices are controlled by centralized server infrastructure, which makes them vulnerable to attack. The decentralized nature of blockchain technology could mitigate the risks current IoT devices present and help secure products still in development.
Solving Deployment Problems
Blockchain technology has the potential to solve serious problems in the IoT world, but it will succeed in doing so only if implemented properly. Developers must understand the needs of their customers, the solutions those customers have previously deployed to meet those needs, the degree to which previous solutions have succeeded or failed, and who the various stakeholders are within any given environment.
When deploying a network of IoT sensors to monitor warehouse temperatures, for example, who needs to have access to that log to ensure that the environment is kept at the proper temperature? Who should receive alerts if temperature thresholds are exceeded, and should the IoT solution be able to adjust the temperature in the room, or should it be limited to sending a warning?
Blockchain technology isn’t a panacea. It can’t automagically provide a solution to a problem if that problem hasn’t been well articulated and constrained to match the specifics of the situation at hand.
Some legacy embedded systems may be capable of interfacing with blockchain-secured IoT products, while others may need to be upgraded or replaced. Developers will have to contend with shifting from a centralized server infrastructure to a decentralized model capable of handling input from dozens, hundreds, or even thousands of devices. Flexible, scalable solutions are required if these implementations are to be successful.
We now turn our attention to SPARKL and its unique ability to connect legacy systems with smart, blockchain-enabled policies and sophisticated control systems.
What is SPARKL?
SPARKL consists of two key components: the SPARKL Sequencing Engine, and the Clear Box configuration system. Clear Box is explicitly designed to interoperate with multiple systems simultaneously and offers a single point-of-access to all of the information developers need to make systems work together—even if those systems normally don’t communicate with one another.
Clear Box is flexible, can support multiple blockchain implementations simultaneously, and can also call third-party services or applications (Figure 2). It also allows for fine-grained permission settings to ensure that only users who are cleared to see certain data sets have access to them.
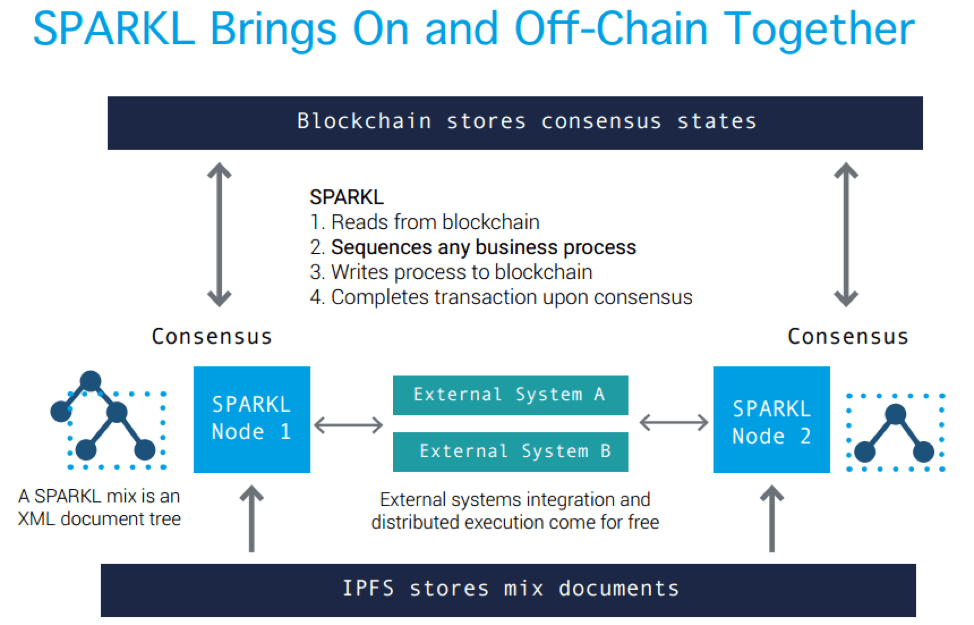
This flexibility solves a major problem when considering deployment of IoT devices and blockchain technology, namely the difficulty of combining them with legacy systems. Instead of attempting to implement an entirely new control system with a unified set of hardware and software solutions capable of addressing every single use case, Clear Box and the SPARKL Sequencing Engine can communicate with solutions that are already in situ, gather data from these multiple sources, and execute whatever instructions the end user has defined. If Clear Box is the solution that defines policies or behaviors, the SPARKL Sequencing Engine drives those policies and behaviors across the entire system.
SPARKL has released a Proof of Value (PoV) demonstrating how blockchain technology and its own services can be used to build smart contracts for the reinsurance market. SPARKL is compatible with multiple distributed ledger projects, including BigchainDB, HyperLedger, and Intel® Sawtooth Lake, with the latter used for the reinsurance write-up (Figure 3).
Sawtooth Lake is a modular distributed ledger platform that’s designed for versatility and scalability, with support for a wide range of consensus models. Consensus, in this context, refers to the process of building agreement between systems that mutually distrust each other.
The goal was to create a set of smart policies that could account for different trust relationships between participants, interface between legacy and non-legacy systems, support a comprehensive automated policy workflow, and transparently record transactions in a manner that would be visible to all parties. To function effectively, the smart policies must be able to evaluate complex conditions, properly group claims, apply any policy limits, calculate and process premium payments, and keep the transaction ledger updated appropriately with each of these steps.
The result of this process isn’t just another Band-Aid slapped on creaking infrastructure: Executed properly, SPARKL can be used to connect legacy and cutting-edge systems to create new blockchain-based smart contracts and policies that automate contract enforcement while simultaneously providing all stakeholders with the documents they need for record-keeping and regulatory purposes.