Three Pitfalls of Automation Design

In the world of industrial IoT, consistent, reliable data is the name of the game.
But automated machines are vulnerable to inefficiency, downtime, and even failure. And in highly automated factory environments, the repercussions of malfunctioning equipment can be costly. For example, corrupt or lost data in an automated inspection system can bring an entire production line to a standstill.
On the other hand, proper use of data can help minimize or prevent these occurrences altogether. But automation engineers need to avoid common mistakes when designing industrial IoT technologies and data architectures into next-generation automation systems.
Three Common Design Mistakes
Even though careful planning can add cost during the R&D phase of a project, it’s significantly less expensive than adding features or re-engineering entire electronic systems midstream.
Reliability, security, and remote management mistakes can lead to engineering rework later in the design of data-centric industrial IoT systems.
#1: Choosing Cost Over Reliability
Component selection is a clear prerequisite for industrial automation equipment, given the harsh environments they are deployed in. But many engineering teams are pressured to balance reliability with cost.
Components are often evaluated across a few obvious parameters like operating temperature range, shock and vibration tolerance, and things like program/erase cycles in the case of storage equipment. If a product checks these boxes, the lowest price usually wins.
But there are other, perhaps hidden, factors that can make or break a system design later. One example is how the system performs under fluctuating power supply voltages—common in factory environments. Since IoT systems are highly dependent on data, storage devices must protect and retain data during power spikes, drops, or outages.
#2: Starting Security Design Too Late
Industrial automation devices have traditionally operated on closed operational networks, making security more of a physical concept than an electronic design imperative. Industrial IoT networks need equipment data to be exposed to other business and analytics systems, which opens automation machines to network-borne threats.
“Consider an automated optical inspection system on the factory floor,” said Edison Shih, Senior Business Development Manager at Innodisk. “What if someone hacked into the device and generated erroneous data that could cause the inspection system to fail in detecting faulty products? This could eventually have a huge effect on a plant that began mass-producing and distributing defective products.”
In isolated systems, features like write protect integrated into storage devices can provide an extra layer of security that prevents hackers or malware from altering machine data. This feature must be inherent to the storage technology or vulnerabilities could be exposed that compromise the entire system stack.
#3: Home-Brewed Remote Monitoring & Management
Since factory automation devices are often deployed in dangerous or hard-to-access locations, engineers must consider all of the ways that a device can be monitored and controlled remotely.
Remote monitoring and management requires reliable sensors, local analytics software, and robust network connections. Remote visualization dashboards are also needed for automated alerts and in-depth analysis. Developing these end-to-end platforms can be a greater undertaking than the original system design itself.
By partnering with @innodisk_corp on a modular IoT data storage architecture, the equipment was able to pack up to 300 food items per minute with virtually no downtime, while also achieving a 5-to-10-year lifecycle. @insightdottech
Case Study: High-Production Packaging on IIoT Storage
One industrial automation company was able to avoid these pitfalls in the design of a high-speed food packaging system. By partnering with Innodisk on a modular IoT data storage architecture, the equipment was able to pack up to 300 food items per minute with virtually no downtime, while also achieving a five-to-ten-year lifecycle.
The foundation of the food packaging system is high-endurance single-level cell (SLC) flash technology. Compared to newer, consumer-grade flash technologies based on multi-level cell (MLC) and triple-level cell (TLC) architectures, SLC flash provides lower read/write error rates, can operate over wider temperature ranges, and supports far more program/erase (P/E) cycles.
For example, Innodisk’s SLC-based memory products such as the 3MG2-P SSD deliver as many as 3,000 P/E cycles with a mean-time between failure (MTBF) of greater than 3 million hours. These were implemented on crossover extension cards that allowed the manufacturer to easily drop in storage products based on different technologies and form factors.
But to maximize uptime in the food packaging system, Innodisk backed its memory and storage devices with auxiliary reliability features:
- iPower Guard: Safeguards SSDs from physical damage that can occur from unstable power supply voltages with a startup and shutdown protection mechanism.
- iCell: Extends an SSD’s emergency residual system power from an industry average of 2 ms to 60 ms so that memory can be written from caches to flash memory cells.
- iData Guard: Completes any read or write operations in progress and prevents the SSD from accepting new commands in case of sudden power loss with low-power detection and recovery. Intelligent algorithms kick in just before and after power loss to save data and remap memory tables.
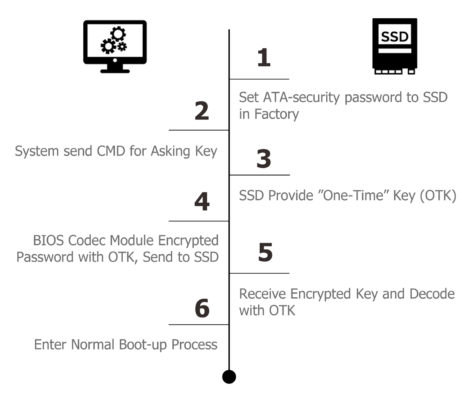
From a security perspective, Innodisk bakes several protection mechanisms into its storage products. These start with an ATA security password that is set during manufacture and stored in a secure area of the drive. This password serves as the foundation for an encrypted key exchange with the host system prior to bootup, and is also used for features such as write protect and pair checking (Figure 1).
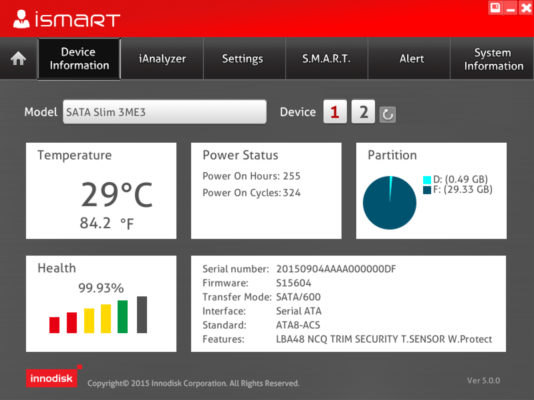
Finally, Innodisk’s iSMART remote monitoring and management software provides metrics on the device’s read/write behavior, wear leveling, temperature, and projected remaining lifespan. Users can even execute security erase functions in case of a breach (Figure 2).
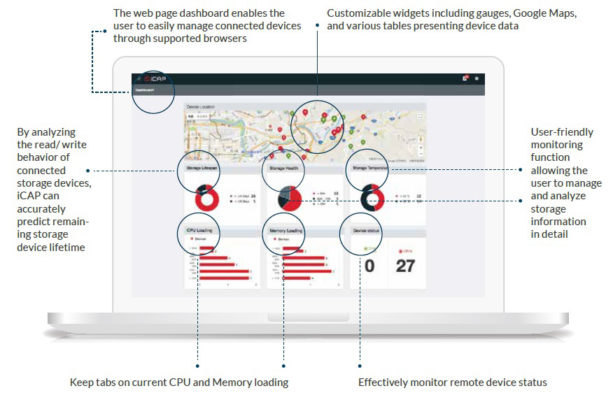
This data is captured and displayed in Innodisk’s iCAP cloud administration platform (Figure 3). And thanks to support for Windows and Linux operating systems, the packaging automation company was able to leverage standard APIs to extend iSMART capabilities throughout the rest of its systems.
Selecting off-the-shelf solutions like iSMART and iCAP can save design teams significant time and cost. The only prerequisites are 2 GB of system RAM and a host processor capable of at least 1 GHz clock speeds. This level of performance is available on all Intel Atom® processors, which can access Innodisk storage technologies over the native SATA interface.
Advancing Machine Automation with IIoT
Historically, machine automation has been used to replace human operators with self-driven equipment that provides higher levels of accuracy, speed, and efficiency. It allowed industrial organizations to improve worker safety, reduce labor costs, and increase production volume.
But highly automated machines are only as good as the data they rely on. In these connected industrial environments, lost, corrupt, or stolen data can have consequences that are far more severe than the worst accidents in human-powered factories.
To prevent these incidents, industrial automation engineers must do their due diligence from the beginning of the product development lifecycle. Foundational IoT data storage technologies can provide the reliability, security, and management capabilities to help these engineers avoid design pitfalls before it’s too late.