Secure Your Drone From IoT Risks Before It Takes Flight

In the world of embedded systems, security through anonymity has been the norm. But now we’re interconnecting these devices as part of the IoT and opening them up to unpredictable security risks.
Once designers start incorporating connectivity into their systems, vulnerabilities were bound to become the new reality. Common-sense engineering calls for new ways to stress-test the IoT systems, which in many cases use legacy hardware and design techniques from the pre-connected era.
Take, for example, commercial drones, which are increasingly becoming connected, exposing their hardware and software to cyber threats. It’s a classic example of why engineers must think about security-related issues during design, not after.
While safety-critical aspects need to be certified with advanced testing capabilities, it’s nearly impossible to solve most of these problems without some form of modeling on a virtual platform.
Hardware-based testing can be costly and complex. Engineers need to get a device into a state of known vulnerability, which can take days or even weeks, with the potential of physically damaging the hardware.
Exposing IoT Vulnerabilities
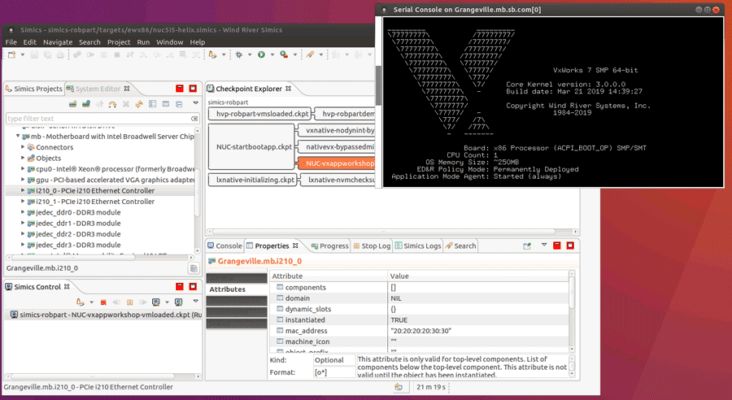
This is where fault injection, or penetration (pen) testing, comes in. A pen test simulates an attack on a drone (or other embedded system) to detect vulnerabilities. Here, developers can use a library of known attacks or weaknesses to inject a fault into the device under test (DUT) and analyze the response (Figure 1).
“There’s an emerging discipline now in the embedded space around preemptive methods for finding security flaws,” said Sean Evoy, Tools and Simulation Product Manager at Wind River. “The problem generally becomes one of how to accomplish this. What are the tools at my disposal to go in and perform this kind of routine pen testing, and more to the point, how do I do this in a way that’s scalable?”
Unlike test rigs that use the real hardware, where failures can be intermittent, a virtual platform gives designers the ability to create a complete and accurate checkpoint of the system at any given time.
A checkpoint of a simulated system lets developers inject a fault into memory and exploit a vulnerability in a piece of hardware or a legacy bus. With this information, designers can see how the system responds. For example, IoT developers can find out how the drone responds if a person with malicious intentions changes a memory value.
Consequently, rather than physically testing the drone, developers create a software representation of the hardware that’s running inside the drone. In other words, they can create a digital twin and run it on a server or network hardware.
A virtual platform gives designers the ability to create a complete and accurate checkpoint of the system at any given time.
via @windriver
Modeling with a Simulation Engine
That brings us to Simics, a toolkit offered by Wind River Systems that lets embedded designers model hardware on a virtual platform at the required level of detail. It can also be used to build a digital twin. Digital twinning, a software concept of creating an object analogous to a real-world entity, provides software-based representation of sensors, telematics, and location systems.
That twin is an abstraction of the embedded system, which can be very small or very large, and it gives designers complete control over the hardware (Figure 2). Simics facilitates scaled simulations, modeling an individual drone, a particular component, or a network of interconnected drones. The only limit is the availability of hardware or servers that designers can use to test these models.
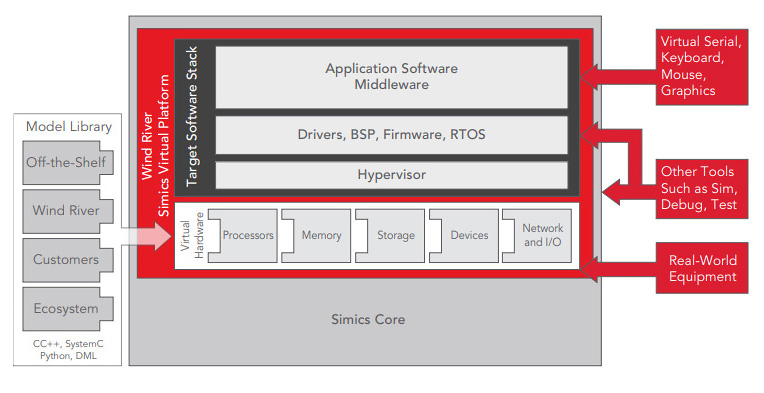
Each model that’s created requires a certain amount of resources, like memory and CPU cycles. The Intel® processors running these drones (or industrial control systems and other IoT applications) can abstract hardware to allow multiple workloads to share a common set of resources.
Furthermore, Intel® Virtualization Technology (Intel® VT) provides hardware assistance to the virtualization software while eliminating performance overhead and improving security.
Simics can also help create a network of virtual platforms—a designer can spin 50 drones and see how they behave when part of a network. “Security experts can fuzz-test the network by introducing noise and simulating a signal loss or component failure on the drone,” said Evoy.
He added that unlike the testing on actual hardware, which gathers data for a fixed amount of time to catch a failure, the system clock for simulation could run both forward and backward to find the root cause of the problem.
“Simics lets designers inject the fault and run it backward until they isolate it. Then they can approximate the cause of that fault,” he said.
Extensive IoT Cybersecurity Testing
The bottom line is that extensive security testing during development and prototyping stages can save designers time and money—ensuring drones will work properly before they take to the air. Plus, testing cybersecurity in controlled simulation environments lets developers catch consistently emerging security vulnerabilities and quickly fix the problems.