4 Tricks for Migrating Critical Systems to the IoT
Connecting embedded systems to the IoT presents two main problems. The first is scalability, both across legacy systems and forward to meet future requirements. The second is security, both across the infrastructure that connects the system and forward through the lifecycle of the system.
To a surprising degree, these problems can be solved by borrowing software-defined infrastructure (SDI) concepts—such as virtualization and workload consolidation—from the telecom sector. Systems based on SDI offer a level of flexibility and scalability that hardware-centric architectures cannot match. This new infrastructure enables legacy systems to quickly migrate to the IoT, and supports rapid adoption of new capabilities over time.
SDI can also strengthen security. The nature of cyberattacks is constantly changing, but it is difficult to update a hardware-centric system. In contrast, a software-focused infrastructure offers the flexibility to accommodate rapid change. What's more, a software-based approach can better accommodate new capabilities such as real-time cybersecurity analytics.
1. Hardware Consolidation
According to Alex Wilson, director of market development at Wind River Systems, Inc., there are two dimensions to SDI in an embedded context. The first is what he calls east-west consolidation—that is, the merging of functions within an industrial plant onto a shared platform (Figure 1).
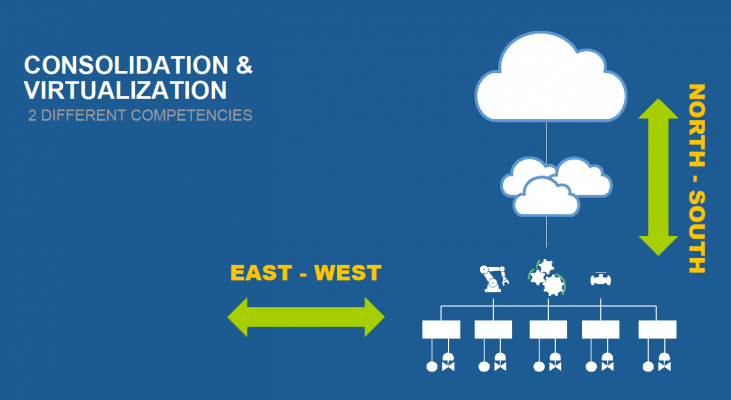
Workload consolidation, he said, “reduces the number of subsystems we have and provides savings across the enterprise.” It's important to keep in mind that the main characteristics of east-west systems are the need for real-time control and functional safety on the shop floor.
Keeping this in mind, virtualization allows functions within a consolidated system to be isolated from one another (Figure 2). “You will likely want to isolate your critical code from the rest of your software, including your IoT communications interface, to minimize exposure of your critical software from security threats,” said Wilson.
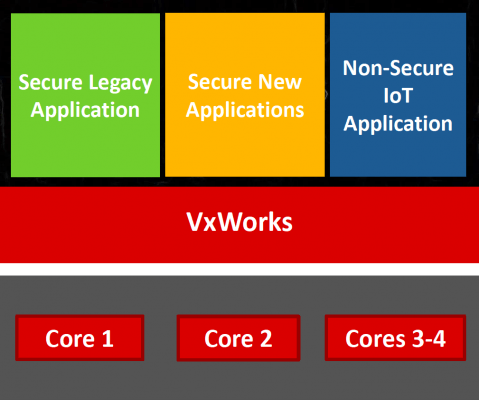
Plus, new applications can be added without re-certification of existing functions—reducing the downtime involved with upgrades. “Virtualization gives us the ability to update and validate new functionality before retiring old functions,” said Wilson.
2. Software-Defined Infrastructure
Next is virtualization of what Wilson calls the “north-south” connection between the plant and the cloud. As he sees it, this infrastructure needs to be less hierarchical and allow for more processing at the edge (versus doing it all in the cloud). This includes the use of fog computing to apply analytics close to the edge, using the cloud only if absolutely necessary.
This change reduces latencies and bandwidth usage. “We're looking more at the flattening of the topology,” said Wilson, “running services on standard server equipment, maybe in a local cloud, or fog, or up in the cloud itself [if needed].”
The main characteristics of virtualized north-south systems are scalability, performance, and high availability. According to Wilson, this provides “the ability to deploy services where we need them, on demand, at any time.”
Across the newly virtualized infrastructure, software such as Wind River Titanium Cloud can be used to manage applications, security, and connectivity. Titanium Cloud is a carrier-grade virtualization suite that was built specifically for systems that require high reliability, performance, and security.
3. Lifecycle Security
So far we have discussed the value of virtualization acrosssystems. But what about the need to scale forward through the lifecycle of the system? Many IoT devices are “abandoned” without active updates and so over time they become vulnerable to new attacks.
To avoid these risks, developers can monitor threat alerts from services such as CVE, US-CERT, and NIST that are received, and apply patches as soon as they become available. “Using these databases ensures you don't fall into the traps that others have,” said Wilson.
4. Real-Time Security Analytics
While it's critical to keep up to date with databases, this is a responsive approach. Proactive measures are even better. That's where real-time analytics tools such as AXON Predict from Greenwave Systems can help.
AXON Predict allows systems to be self-monitoring and autonomous in certain actions. For example, it can monitor for data leaks and insertion of malicious code, check for any potential data taint, and monitor communications channels for unnecessary communications (Figure 3).
If suspect communications occur, the platform can either alert the operator or close down those channels directly. “This is really leading edge in how we can offer cybersecurity,” said Wilson.
No Sitting Still on Cybersecurity
The IoT revolution is fraught with issues, from the migration of legacy systems to ensuring data is secure. Tools and techniques such as virtualization and hardware consolidation can ease the transition, and new real-time cybersecurity analytics techniques can enable a more proactive approach to threat detection and management.