Four Steps to Secure Linux-Based Systems
Today's connected devices are more vulnerable than ever to security threats, but the intricacies of today's platforms can make it difficult for developers to cover every potential entry point. To help mitigate the threats on Linux-based systems, Wind River, an Intel® company, came up with a four-step process that OEMs should adhere to: monitoring, assessment, notification, and remediation.
Let's explore what's happening in today's threat environment before looking at what these four terms mean and how they should be applied.
Identifying the Most Common Vulnerabilities
Attacks come in many forms and use various entry points. McAfee Labs recently released a chart depicting the most prevalent attack types (Figure 1). Each attack type comes in several flavors, as there's usually more than one way that they can be configured or camouflaged based on the experience, resources, and determination of the hacker. While some threats are more prevalent than others, a developer needs to protect against all vulnerabilities.
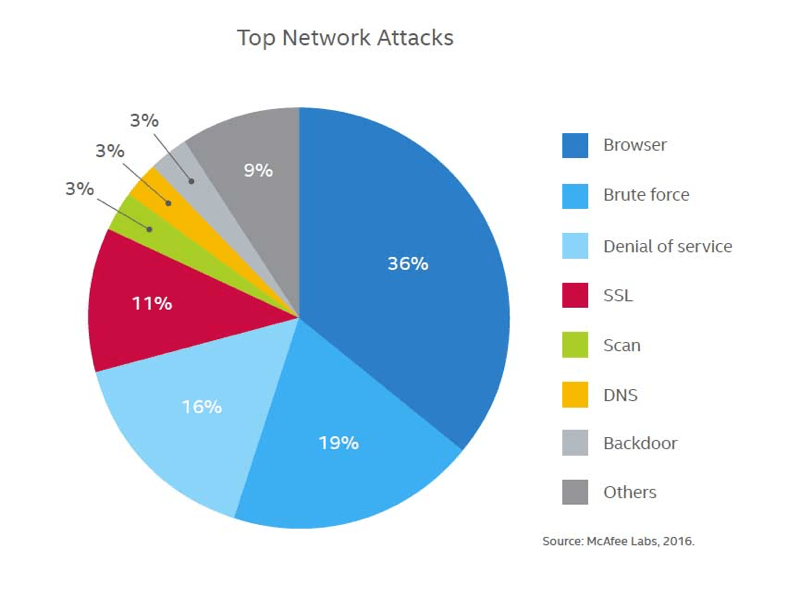
Identifying common vulnerabilities and making the necessary updates to mitigate threats is often beyond the capability of device developers and manufacturers. That's one reason using a Linux-based system from a trusted vendor is advantageous. Wind River's proven four-step process for resolving Linux vulnerabilities can determine which data to monitor, when to act, what to fix, and how to keep the code base updated. If implemented with care, it can have a significant impact on schedules and project cost.
Four Steps to High Security
Let's look at Wind River's four steps in more detail:
1. Monitoring
Monitoring involves looking deeply inside your own strategy. Obviously, this alone doesn't solve any problems, but it should provide lots of insight as to whether your strategies hold water. It also helps to compare against known good models, including those that come from respected sources that specialize in finding Linux vulnerabilities.
For example, Wind River's security team is constantly monitoring the Common Vulnerabilities and Exposures (CVE) database at cve.mitre.org for potential issues affecting Wind River® Linux and Wind River® Pulsar™ Linux. By also monitoring specific security notifications from U.S. Government agencies and organizations like NIST, US-CERT, as well as public and private security mailing lists, users can receive email alerts from each of these organizations whenever a new security threat arises. All the kernel features, user packages, and Linux tools supported in standard Wind River Linux distributions are monitored for security vulnerabilities against the incoming reports.
2. Assessment
As soon as a potential threat is uncovered, the level of danger associated with the threat, as well as which parts of the system are exposed or vulnerable, must be assessed, by either the system, or the persons in charge of threat assessment. That vulnerability should be ranked in order of importance based on how severely it could impact system performance or expose data. As you'll see in subsequent steps, assessment is vital to enact the proper steps in the correct sequence.
3. Notification
Once assessment is complete, the system should report back to any affected subsystems or users. This report must provide sufficient detail about the vulnerability, as well as a plan to thwart the threat. This dovetails into the remediation step. The notification step may involve employing outside tools and people. This is a determination that would be made based on the assessment. But the key element of this step is the timely handling of notifications to keep damage or data loss to a minimum.
4. Remediation
Finally, the remediation step must occur, triage style. Based on their severity, threats are either dealt with immediately or handled in a timely "bug fix" that comes later. Once a system is back online, the entire process begins again. In some cases, though, a system can't come off-line in the first place, making the steps a little tricky. For this reason, less-severe vulnerability patches in Wind River Linux are delivered via monthly product updates.
In addition, Wind River Linux provides six-sigma uptime, and is a Yocto Project-compatible solution that meets the registration requirements of the Linux Foundation's Carrier Grade Linux 5.0 spec. Depending on your application, adherence to such important specifications can be a big timesaver.
Looking Forward
While these steps won't ensure that all threats are avoided, they will help you mitigate risk and reduce a system's exposure. Pick the Linux OS provider that best suits your application needs and be sure it's following the steps outlined here.