Secure Converged 5G Networks Before They Deploy
5G networks hold enormous potential for IoT applications. But escalating security concerns threaten to stifle performance before 5G even deploys.
The challenges start with IoT device density. 5G can support 2.6 million devices per square mile, and every connection must be secure. And the list of security functions keeps growing. Packet inspection, key generation and storage, and end-to-end encryption are just a few issues network architects must consider.
These security requirements can create serious bottlenecks that hamper performance. For instance, a single SSL/TLS handshake can consume up to 2 percent of a processor’s resources and add 5 ms of latency.
Security demands can also increase system costs. Deep packet inspection (DPI), for example, often requires the addition of a dedicated multicore processor or hardware accelerator.
CSPs looking to capitalize on 5G should be wary of the ways security can impact their systems, as well as solutions that can offset those limitations.
Transforming 5G Security Bottlenecks into Floodgates
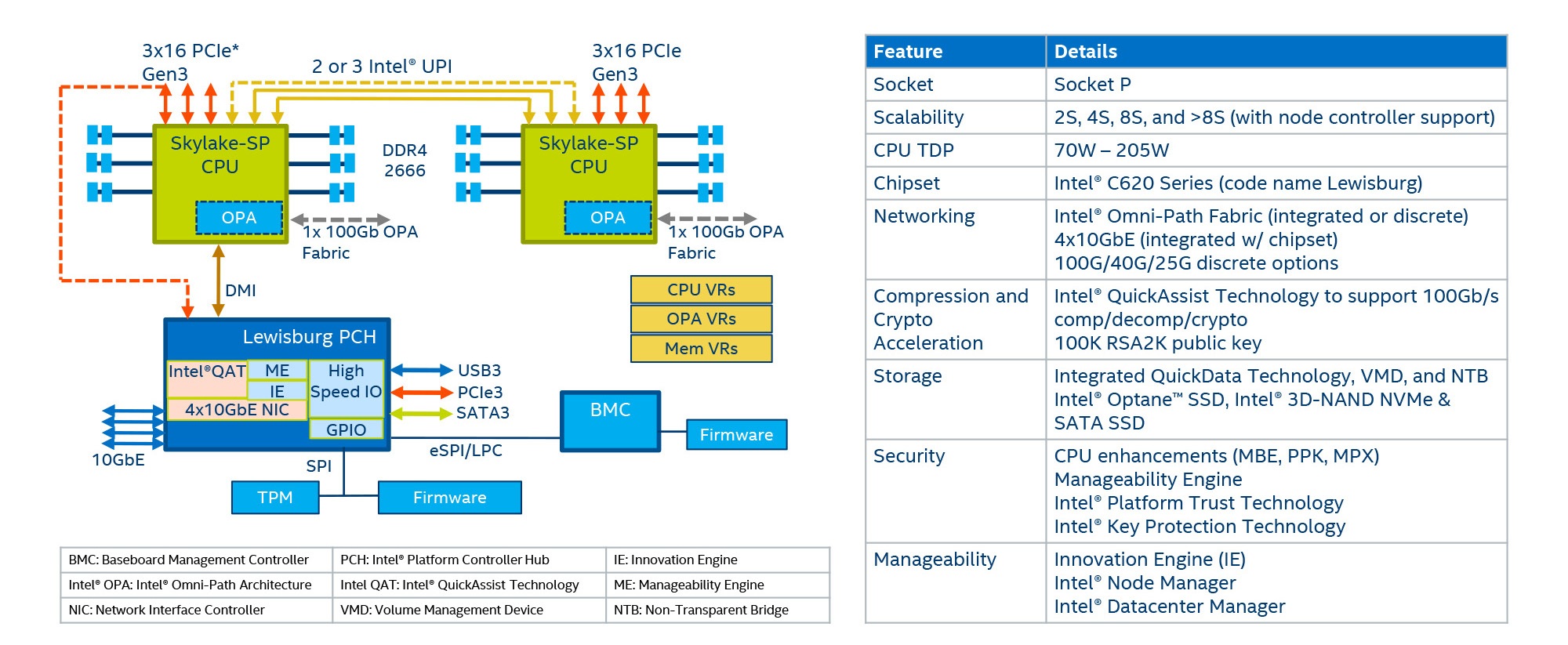
Intel® Xeon® Scalable Processors offer one possible solution. The new processors support as many as 224 cores and 12 Terabytes of memory in an eight-socket configuration (Figure 1), delivering the packet processing and control plane resources required for secure 5G network operations.
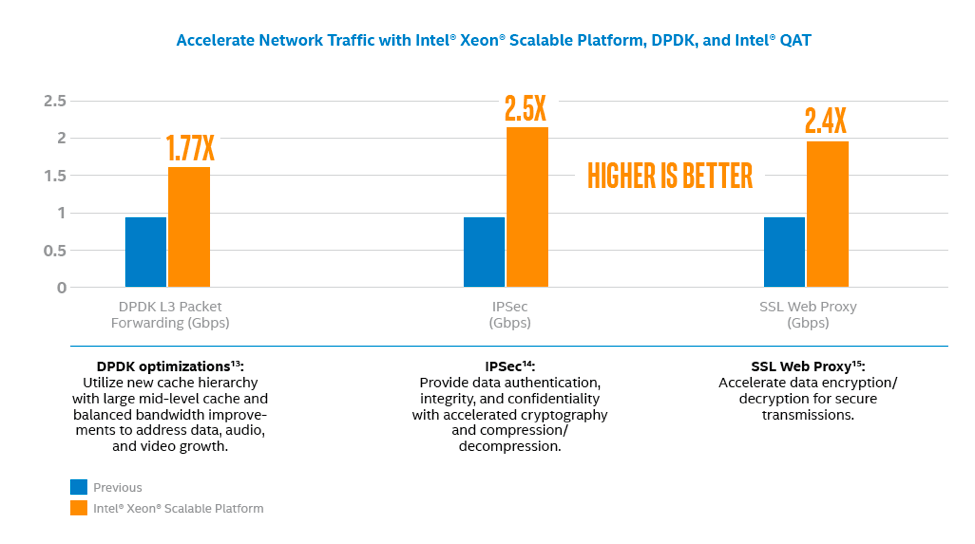
The new chips offer impressive performance gains across a range of 5G tasks. These include a 1.77X boost in L3 packet forwarding, a 2.5X acceleration in IPSec performance, and a 2.4X improvement in SSL Web Proxy transmissions (Figure 2).
The Intel® Xeon® Scalable Processors also support 1.5X more VMs per server than previous-generation processors. As a result, CSPs can consolidate multiple server platforms, reducing the cost and complexity of 5G rollouts.
Advanced Network Security Performance From the Ground Up
New Intel® Xeon® processors include several significant architectural enhancements that enable them to achieve the above benchmarks. In particular, Intel® Advanced Vector Extensions 512 (Intel® AVX-512), a revamped chip architecture, and updated interconnect and fabric interfaces benefit 5G network security.
Intel® AVX-512 is a new set of instructions designed to optimize ultra-wide (512-bit) vector operations such as those used to generate cryptographic primitives. The instructions are supported by two 512-bit fused multiply-add (FMA) units per core, which help deliver double the FLOPS per clock cycle of AVX-512 over its predecessor.
This performance increase results in 3.1x faster hashing of SHA algorithms and 2x faster processing of Reed Solomon Erasure Code when leveraging Intel® AVX-512.
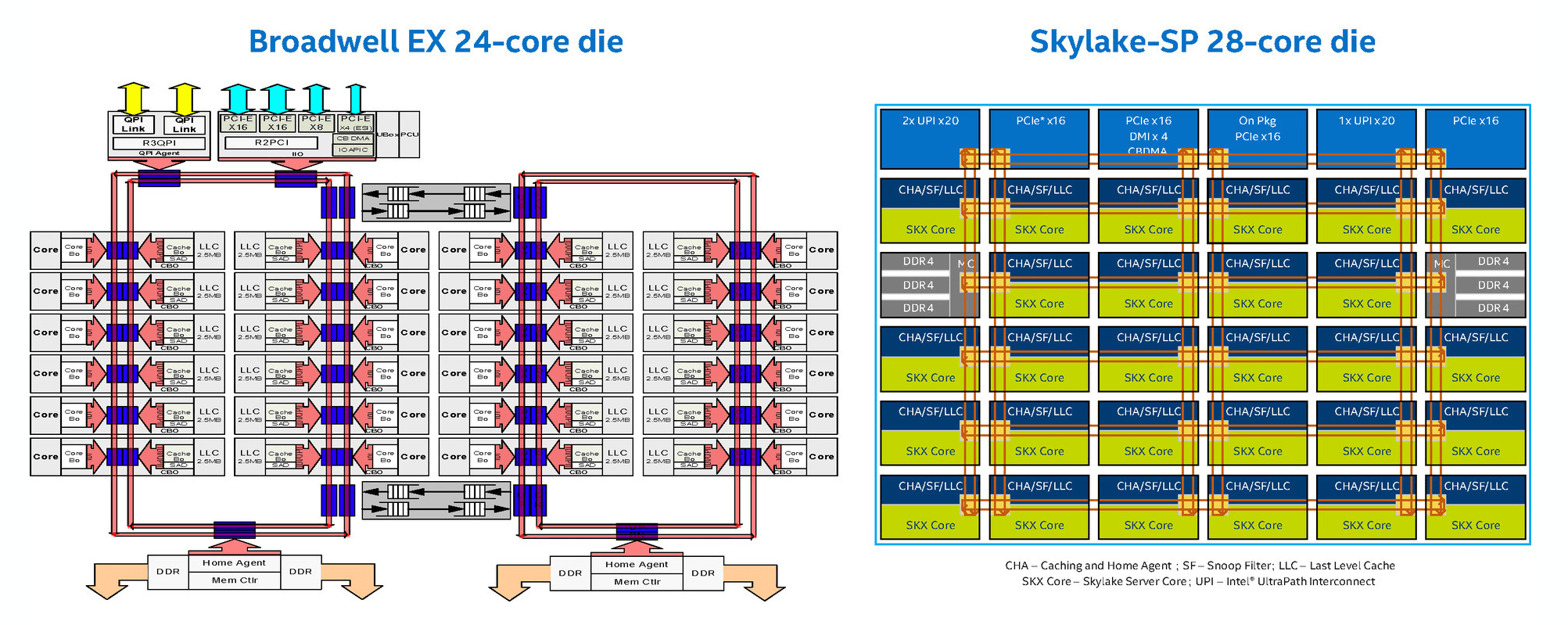
To prevent the powerful new Intel® Xeon® from becoming I/O bound, the 14 nm Skylake-SP microarchitecture has also been redesigned in a mesh topology (Figure 3). The on-chip mesh interconnect facilitates higher bandwidth, lower latency core-to-core communications. This helps optimize task scheduling/transfers and reduces energy consumption in network servers and UTM systems.
Off-chip I/O has also been updated to extend performance beyond a single processor. For starters, the new Intel® Xeon® Scalable Processors include up to 48 PCIe 3.0 links and six memory channels that support 2666 MHz DDR4 DRAM. The latter equates to a 50 percent increase in memory bandwidth over the last generation.
But the main I/O enhancements for massively scalable 5G network infrastructure are in socket-to-socket and system-to-system connectivity.
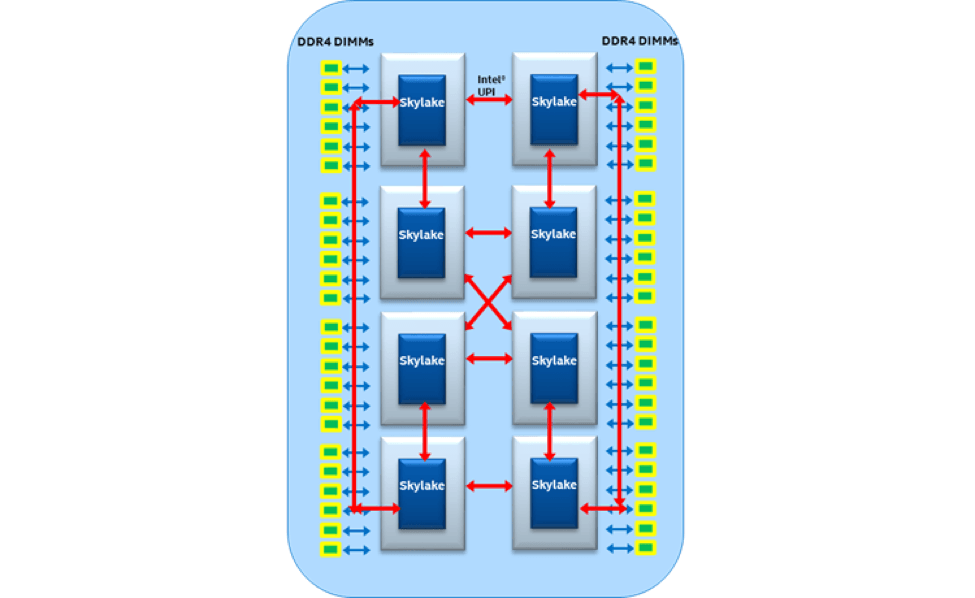
Between sockets, the Intel® Ultra Path Interconnect (Intel® UPI) provides a cache-coherent, 10.4 GTps data path between CPU sockets (Figure 4). The interconnect can scale to support up to eight processors per system under a single shared address space, with each Intel® Xeon® Scalable Processor, including two or three native Intel® UPI links.
To enable and secure 5G deployments that consist of millions of devices per square mile, the Intel® Omni-Path Architecture (Intel® OPA) fabric supports 10,000 or more nodes for each high-performance computing (HPC) network cluster.
Intel® OPA is the successor to Intel® TrueScale Fabric, and positioned as the next-generation alternative to InfiniBand. While its cost and 100 Gbps line rates are currently comparable to competing technologies, Intel® OPA’s feature set is the key differentiator for 5G networks:
- Traffic Flow Optimization – Higher-priority packets can preempt lower-priority packets, regardless of packet ordering
- Dynamic Lane Scaling – Link continuity is maintained in case of lane failure
- Packet Integrity Protection – Link-level error checking is applied to all data packets, allowing transparent detection of, and recovery from, transmission errors
Intel® OPA is integrated in the package of Xeon® Scalable Processors to ease the deployment of HPC networks and security applications.
A Companion for Near-Zero Encryption Overhead
To maximize processor performance, the Intel® C620 Series Chipsets (formerly codenamed “Lewisburg”) offload cryptographic workloads from the main processor. The chipsets come pre-equipped with Intel® QuickAssist Technology (Intel® QAT) to provide network security features, including:
- Symmetric encryption and authentication
- Asymmetric encryption
- Digital signatures
- Lossless data compression
- RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC) functions
In addition, the chipsets incorporate Intel® Key Protection Technology (Intel® KPT). Intel® KPT is a new feature that helps protect sensitive private keys stored in hardware from software and probing attacks (Figure 5).
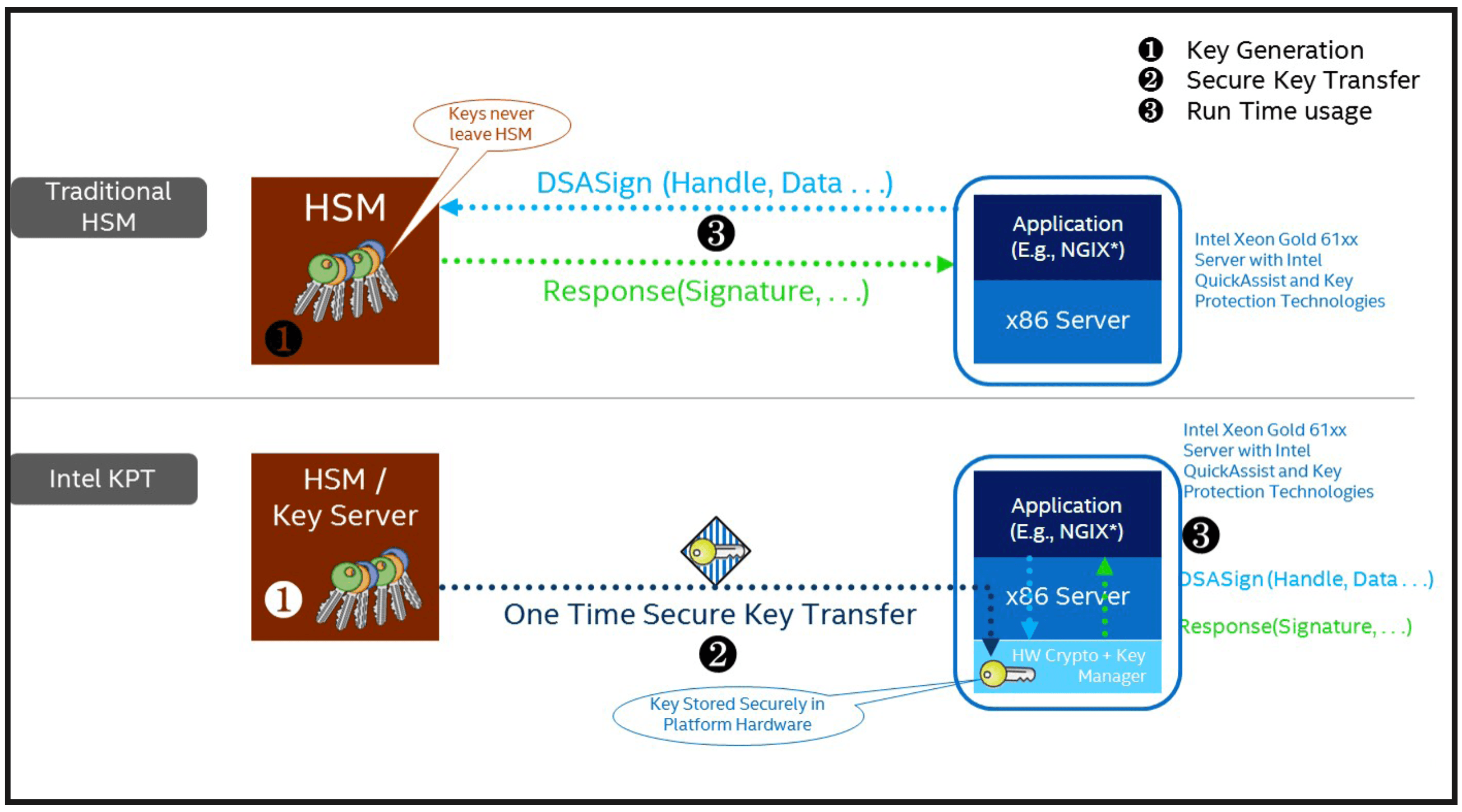
Intel® KPT works with Intel® QAT to enable near-zero encryption overhead for data-at-rest and data-in-motion, reducing the need for dedicated hardware security modules (HSMs).
Intel® QAT also supports all standard device virtualization models. This extends the features of Intel® QAT and Intel® KPT to all virtual machines (VMs) running in a system.
5G and the Converged Infrastructure Shift
5G network architectures are hallmarked by “converged” infrastructure. In this paradigm, dedicated network appliances are replaced with systems that handle multiple network functions simultaneously.
As a result, network equipment providers (NEPs) are bringing standards-based hardware platforms to market that support networking, storage, security, and other functions in a single package.
For instance, the ADLINK Technology MCN-2610 is a compute node based on Intel® Xeon® Scalable Processors (Figure 6). It provides 4×10 GbE lanes to maximize the performance benefits of Intel® Xeon® Scalable Processors in UTM systems and 5G network servers.
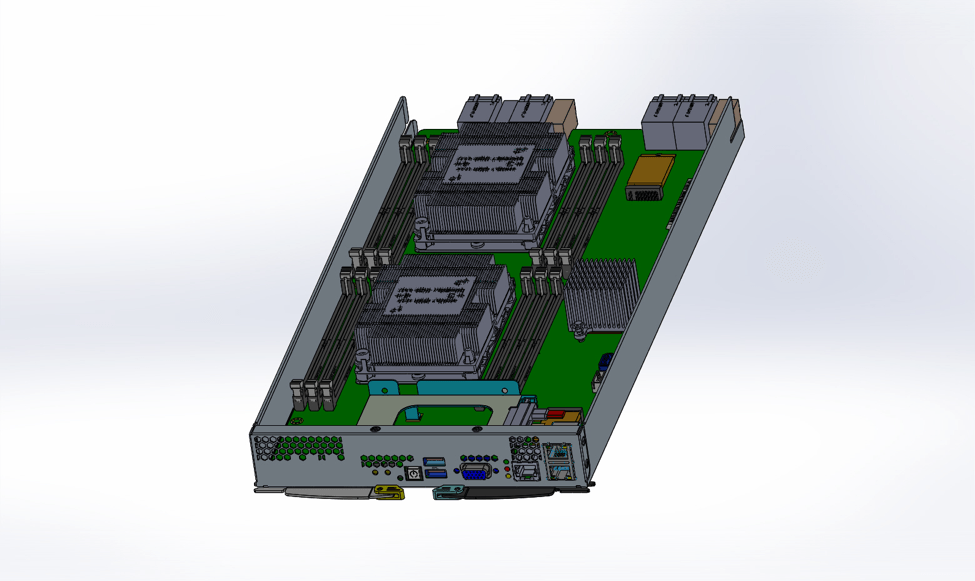
The MCN-2610 adheres to the Open Compute Project (OCP) OpenSled specification. OpenSled is derived from ADLINK Technology’s Open Compute Carrier-grade Edge Reference Architecture (OCCERA), which emphasizes NFV and SDN principles on top of modular industrial design standards.
The standards-based approach of OpenSled allows modules to provide on-demand resources in converged infrastructure platforms. For example, an MCN-2610 module in a UTM system could dynamically switch between DPI and general-purpose routing as demands change.
Such architectures will help ease the transition to 5G network architectures.
Secure 5G Networks Before They Deploy
5G networks have the potential to enable entirely new ecosystems and services, thanks to significant increases in performance. These benefits apply to burgeoning IoT opportunities in addition to traditional networking applications.
CSPs looking to capitalize on 5G benefits should be wary of the ways security can impact the performance of their systems, as well as solutions that can offset that overhead.
With Intel® Xeon® Scalable Processors and compute nodes like the MCN-2610, they need look no further in the transition to converged 5G infrastructure.