How Systems Integrators Can Become IoT Security Heroes

In the era of Industry 4.0, smart factories are making huge leaps in performance by connecting and digitizing production equipment. Yet as companies connect more systems and devices, they are also creating enormous IoT security challenges.
One major problem: Many manufacturers assume that security falls to systems integrators (SIs), but SIs in turn assume that the manufacturers or even the end-clients themselves are handling it—and no one talks about it. Because there is no cohesive security strategy, vulnerabilities are all but guaranteed to accumulate.
It’s a perfect recipe for cyberattacks, with crippling financial damages from data theft, corporate espionage, or even ransomware attacks that hold entire infrastructures hostage.
But systems integrators can prevent all this havoc—and become heroes for their industrial customers—by taking the lead on IoT security.
Mitigating the IoT Security Challenges of a Piecemeal Approach
No one intends for this to happen, but it’s easy to see how it does. Many shop floors are automated one system at a time, notes Jan Ludwig Tiedemann, Senior Solution Architect at secunet. This can lead to a proliferation of DIY setups. In fact, Tiedemann often sees manufacturing environments with hundreds of one-off Raspberry Pi-based systems sprinkled across the shop floor.
While this approach can be cost-effective in the short term, it precludes any kind of holistic security strategy. That means you can end up with a system that’s full of security holes, which build up over time until you end up with an unmanageable mess. In the end, the manufacturer is left vulnerable to attacks and production disruptions.
Compounding the issue is the fact that many companies have a false sense of security about their security. In other words, they may be completely unaware that what they’re doing is insecure.
“secunet edge allows companies to reduce the risks inherent in implementing modern #DigitalSolutions while embracing their advantages.” @jantdm @secunet_AG
Tiedemann points to the experience of one food processing company as an example. Their production lines were full of equipment running old software with a known vulnerability, but the company was oblivious to the risk. Then a hacker released a ransomware attack—and every vulnerable machine was rendered inoperable in a matter of minutes.
Not only did this halt production, it created real-life hazards. The label-printing system was taken out in the attack, destroying its labeling history. As a result, the company would have been unable to track already-shipped products in case of a recall.
Another issue leading to security weakness is that manufacturers expect SIs to keep budgets as low as possible. Tiedemann finds that SIs may be reluctant to mention the need for better security because of its perceived additional cost.
“It often becomes inconvenient for either side to take the lead, so then it becomes a ‘don’t ask, don’t tell’ situation, where no one takes charge,” he explains.
Potential downtime is yet another issue. Tiedemann saw one company all but ignore an attack, instead handling it minimally with a piecemeal approach. The risks of leaving their equipment exposed simply did not outweigh the costs of halting production for a cleanup. As a result, the company continued to work with the attackers still in their systems—a veritable sword of Damocles.
An Industrial PC With IoT Security Built In
Fortunately there’s a solution to these issues: Start with a platform that has security built in. That’s where secunet comes in. As a specialist in areas with unique security requirements—such as industrial IoT, government, and healthcare—secunet saw the need for a truly secure edge solution. The resulting platform secunet edge is designed with a security-first approach.
At the heart of the platform is hardened hardware, including a secure element that serves as a trust anchor for container applications and data security. This tamper-proof chip is FIPS140-2 Level 3 or BSI CC L3 EAL 5 certified, allowing remote users to confidently attest that they securely store and handle sensitive keys to cloud services or similar applications.
The hardware is complemented by a secure software platform and an application environment in which apps are encapsulated in containers, an approach that also prevents breaches in one container from affecting others. These applications enable not only security—such as an automated identification of anomalies in network traffic—but also key systems functions. These functions include transfer of machine data to back-end and external services, and the remote control of connected systems.
Because it is based on powerful and reliable Intel® processors, secunet edge can execute a wide range of existing applications in addition to its security software. Thus, SIs can create a highly integrated automation solution that is at the same time highly secure, convenient to use and cost-effective.
“secunet edge allows companies to reduce the risks inherent in implementing modern digital solutions while embracing their advantages,” Tiedemann says.
What’s more, secunet provides services to keep their platform up-to-date. This approach means that SIs don’t have to worry about their systems losing protection as new vulnerabilities are discovered and don’t have to maintain all of the underlying technology stack themselves.
Instead, secunet provides updates for the operating system and other parts to proactively prevent any security gaps and add new functionality. As platform maintainer, secunet also runs security analyses of the software supply chain and regularly performs penetration tests for verification.
Retrofitting to Preserve IoT Security at Reduced Cost
Of course, securing the factory is not just a question of protecting new systems. Existing assets must be locked down as well.
One common concern is how to provide protection while avoiding costly equipment replacements. Older machines often have specialized, outdated protocols. This makes it difficult to connect legacy systems into a modern IoT environment, where access to the cloud and other IT domains is a must.
To address this question, secunet partnered with PTC, an expert in industrial protocols. By including the PTC Thingsworx middleware on the platform, secunet edge can speak both languages—industrial IoT and cloud. This preserves the free flow of data, while still keeping the legacy machine behind a protective wall that isolates vulnerabilities.
For example, one manufacturer that creates machines for printing and counting banknotes realized that while the machines were designed to run for decades, the operating systems had become outdated. Rather than abandoning the machines and the capital investment they represented, secunet helped the organization update its IoT security, therefore keeping the existing equipment while providing a cutting-edge solution.
“This is the classic use case – retrofitting machines by implementing compensating measures to protect them, rather than throwing them away,” says Tiedemann, adding that this proactive measure may ultimately prevent millions of dollars in damages. (Figure 1)
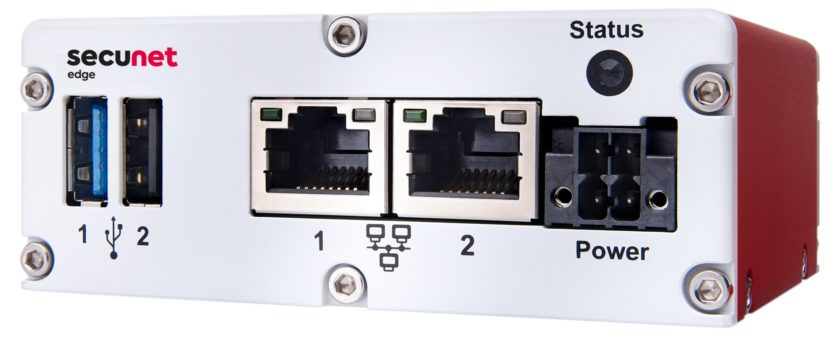
Looking forward, Tiedemann sees his company’s partnership with Intel® as a key to ongoing innovation. “Intel has a long history in IT and also provides superior computing power at the edge, something most other alternatives cannot,” says Tiedemann. For example, secunet will offer an even higher-performance appliance with an Intel® Core™ i5 processor in the near future.
“Intel allows us to be on the forefront of digital transformation with services that others can’t yet offer.”