How Amazon Does Scalable Security on a Budget
The need for IoT security is obvious, and the core principles of security are well known. But developers often lack the time and resources to do security right.
Time-to-market and cost pressures are the main culprit. Developers often face an uphill battle trying to convince management that it's worth investing in security.
Even pointing out risks like a production line getting shut down or a back-end network being hacked may not be enough—particularly if your company is new to network-connected devices and lacks firsthand experience with security failures.
Yet the establishment of security best practices as default rather than afterthought is mandatory, as the number of attack vectors is only going to increase.
The complexity of IoT networks is also increasing. True security not only protects your own device from direct attacks, but also guards against back-door attacks from less-protected subsystems in the IoT data chain.
And the threats are continuously evolving. As a result, developers need a way to keep security solutions up to date with the latest patches.
On top of all this, scalability is a problem. Homegrown security solutions have difficulty keeping up with ever-expanding threats, but commercial solutions may be too expensive and heavyweight to make sense for small deployments.
IoT Service Platform Scales in Cost and Capabilities
Amazon Web Services (AWS) IoT Platform offers an interesting answer to these challenges. The platform is a full end-to-end service that lets users connect devices to AWS Services and other devices, secure the data and interactions, process and act upon device data, and let applications interact with devices, even while offline (Figure 1).
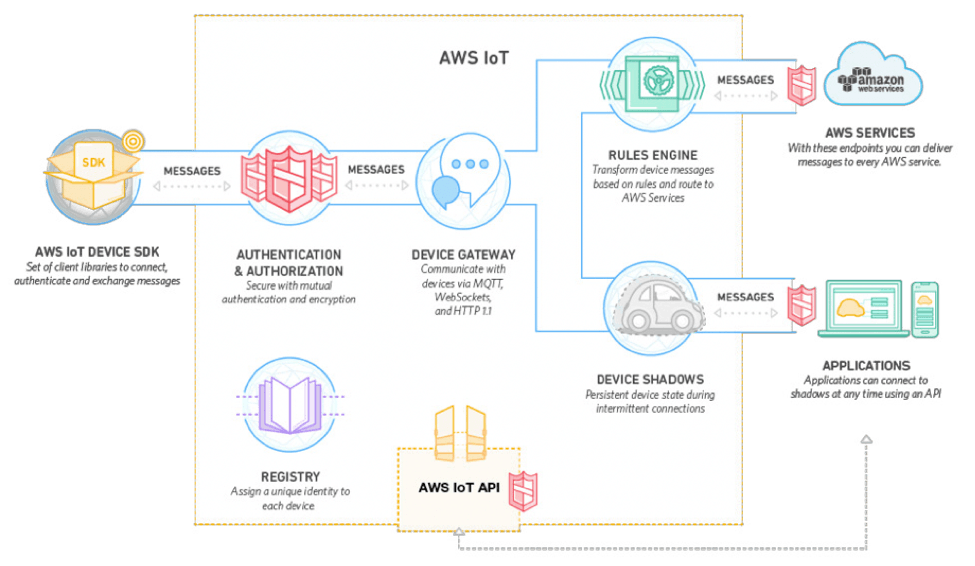
It comprises six main elements, from left to right:
- A device-side SDK with connectivity and authentication libraries
- Authentication and authorization services that limit exchanges to devices with proven identity
- A registry that establishes a unique identity for each device and tracks metadata about the device
- A device gateway that ensures secure and efficient communications, both one-to-one and one-to-many
- A rules engine for gathering, processing, analyzing, and acting on data on a global scale
- Device shadows that let users create a persistent, virtual version, or “shadow,” of each device
The AWS IoT Platform is supported by a deep bench of security, identity, and compliance products from AWS. These include SSL/TLS certificates, a cloud directory, key storage and management, access control, and sensitive data classification, just to mention a few.
For developers looking to speed development while being assured of authentication and end-to-end encryption at all points of a connection, AWS IoT Platform has many of the necessary elements. In addition, it can scale to billions of devices and trillions of messages, which should satisfy most users' needs.
