Connect with Confidence: The Future of Healthcare Security

It is said that trust is the critical currency of our time. And when it comes to trust in healthcare data, probably our most sensitive and personal data, that trust-currency attracts a compound interest. It is the health sector that has seen the biggest catalysts in building trust. And it is also the healthcare sector that has the most experience with detractors of trust—the bad actors whose criminal methods continue to improve in sophistication. Of course, there are other catalysts, too, most notably COVID-19.
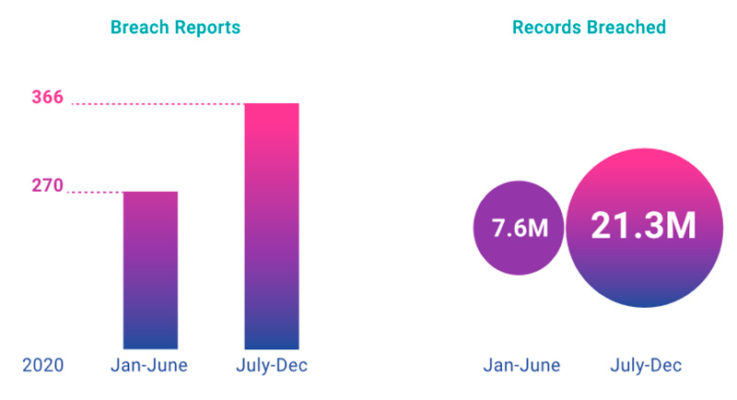
When the pandemic first hit, the healthcare industry quickly accelerated its digital transformation efforts. The lift on restrictions to telehealth and remote patient monitoring are notable. But these advancements also increased healthcare’s exposure to risk. In the past 18 months, 82% of healthcare systems reported an IoT cyberattack, and that number is only expected to rise (Figure 1).
The Allure of Healthcare Data
The pandemic inspired cybercriminals to target our collective health vulnerability. They tried to compromise personal accounts using phishing emails, texts, and messages with COVID-19 as the subject matter. There were even some attacks disguised as COVID-19 intelligence being shared by impersonators of the World Health Organization and Food and Drug Administration.
In addition, there were many new examples of bad-actor collaboration targeting supply chain vulnerabilities. This should come as no surprise when you consider that the bounty for protected health information (PHI) is about 50X more valuable than other stolen data, according to Thomas Finn, Director of Market Development at Medigate, a global leader in healthcare security and clinical analytics.
“If I were a cybercriminal, I wouldn’t focus anywhere else. Healthcare is not only the most vulnerable attack surface, but the most lucrative,” he says. “At the start of the pandemic, relatively few health systems had an accurate inventory of their legacy equipment. And now, given spending on new equipment at greater than 20% CAGR, the problem grows worse. The continued fragmentation of care delivery adds yet another complicating factor to what was already acknowledged as a perfect storm for cybercriminals.”
The Complexity of Connected Healthcare
In terms of connected asset management and security, the complexities of connected health are a function of well-known industry nuances. For starters, most medical devices can’t have agents installed on them without violating the manufacturer’s warranty. They also can’t be scanned. After all, they may be connected to patients. That’s a one-two punch that makes them very difficult to wrap into other managed-device programs. Add the fact that many of the transmission protocols developed by the manufacturers are proprietary. And there’s nothing about their management that is consistent with other smart devices found in other industries.
Having a real-time risk-scored inventory of all #connected assets makes it possible to instantly filter and correlate #threat intelligence and known vulnerabilities to potentially impacted devices. @MedigateLLC via @insightdottech
“Despite how mobile most medical devices are, they were not designed with network security in mind,” says Finn. “And different departments across IT and technology management are held responsible for different types of clinical assets, use different tooling, and obtain different data. They therefore work with different information, which is far from ideal.”
This situation is far too common in most health systems today. And because the use of telehealth and remote patient monitoring is far less restricted now, the challenges are now extending beyond physical walls.
Defense Against Healthcare Attacks
To stop unauthorized device behavior, healthcare organizations must know authorized device behavior. To effectively process threat intelligence, an intimate understanding of connecting devices is essential. For instance, having a real-time, fully profiled, risk-scored inventory of all connected assets makes it possible to instantly filter and correlate threat intelligence and known vulnerabilities to potentially impacted devices. To effectively deal with modern threats, this is foundational capability.
To get there, Medigate has developed a platform capable of discovering and fingerprinting all connected endpoints. In the form of real-time inventory, the company delivers a common data foundation as relevant to IT as it is to technology management and network security professionals. Notably, the company’s reputation is built on doing this for all unmanaged medical devices, which is both difficult and considered the most vulnerable aspect of connected health. It’s not just the visibility provided by Medigate, but by orchestrating the underlying, long-missing data to the entire asset management and security ecosystem.
“Especially when considering the short-staffing challenges in IT and information security, the idea that a single source of truth can be made available to their established workflows in ways that eliminate outdated routines and, importantly, upskill and free them up for more meaningful work, well, that value is hard to overstate,” Finn says.
The Power of Healthcare Partnerships
Healthcare organizations need to work together to create standards that improve overall security governance and compliance within the industry. They need to instantly know the counts and status of care-critical assets, including their security posture and location, so that future unexpected surges in patient demand can be managed more collaboratively.
Medigate is working with Dell, VMware, and Intel® to deliver an integrated approach to healthcare-connected asset management and security. Intel® is used to improve speed and efficiency through accelerated data collection and processing. And working with Dell and VMware, network access control at a software-defined level can be achieved. The combination serves to enable a high-performing virtual environment supporting agile network segmentation policy creation and enforcement.
“Our data collection servers are the fastest and most memory efficient in the industry. Being powered by Intel gives us a significant on-prem data processing advantage. We then move the data to the cloud for fingertip access and full analysis. We’re able to process and present an extraordinary amount of clinical device network data at a hyper-level of detail almost instantly,” says Finn.
Healthcare of the Future
As security provisioning becomes embedded in cross-departmental workflows and becomes part of “our everyday,” major improvements in the overall security posture of healthcare will happen naturally. Operational improvements that drive value for the health system will also occur naturally, including maintenance processes that can begin studying and quickly improving asset utilization rates.
“Shifting maintenance interventions based on elapsed time to actual utilization could be extremely valuable when considering the sub-50% utilization rates that are typical in healthcare. There are numerous new use cases surrounding Alternative Equipment Maintenance programs that could be taken advantage of,” Finn says. “When you know where your devices are, what their status is, and what their utilization is, the possibilities are very interesting.”
Most importantly, security must enable care delivery, regardless of where it executes, not constrain it. Otherwise, clinicians will find workarounds and that defeats the purpose. Fortunately, as healthcare presents a relative green field for modern, integrated approaches to asset management and security, the business value that can be created supports the journey to security operations maturity.
This article was edited by Christina Cardoza, Senior Editor for insight.tech.