4 Big “Make Versus Buy” IoT Decisions
IoT solutions development extends far beyond the manufacturing floor. Systems must be maintained for years or decades after initial deployment, meaning that OEMs need to account for changes in connectivity, device management, security, and application integration over the life of a device.
Supporting all of this technology development in-house can become a significant engineering burden. OEMs therefore must weigh the benefits of developing the complete IoT solutions stack internally or outsourcing portions of it to a technology partner.
When assessing these options, decision-makers should consider four key areas:
- Connectivity
- Device management
- Application integration
- Security
The following article dives deeper into these four areas by asking strategic “make versus buy” questions.
1. Connectivity Management
The IoT networking landscape is constantly in flux.
The low-power, wide-area network (LPWAN) segment is a good example of this challenge. Standards such as LoRa, Sigfox, LTE Cat-M1, as well as NarrowBand IoT (NB-IoT), all have technical advantages and disadvantages based on application requirements.
With LPWAN technologies, OEMs must also consider the geographies they intend to sell product in, both now and in the future (Figure 1). Given the similarity of these technologies, it is likely that one or more are displaced in certain regions in the coming years.
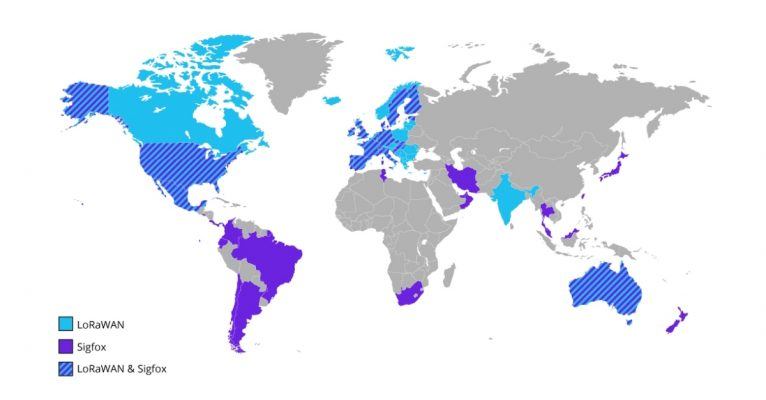
Another aspect of the IoT connectivity challenge underscored by the LPWAN sector is the rapidly changing nature of new and emerging standards. The 3GPP's NB-IoT standard, for instance, recently transitioned from Release 13 of the specification to Release 14, which adds feature enhancements and corrects some of the technical inconsistencies resulting from the initial release being rushed to market.
Faced with this type of networking environment, managers must evaluate the capacity of their engineering teams before embarking on development projects. Questions to ask that can provide structure during this evaluation process include:
- Do our internal networking resources enable us to select, support, and scale the connectivity technology that best serves our use case?
- Are our internal networking resources equipped to handle emerging technologies or drastic changes in the connectivity landscape in the future?
2. Device Management
Device management maintains the functionality, security, and services of an IoT deployment over its lifecycle, typically through the use of over-the-air (OTA) updates. The platforms that facilitate device management must offer capabilities such as provisioning, authentication, and configuration for a large, fluctuating number of remote devices.
Device management platforms are often developed and hosted in the cloud, which falls outside the expertise of most device OEMs. For those considering an in-house design, or even evaluating off-the-shelf IoT platform solutions, reviewing these discussion points can save time, money, and engineering re-work later in the IoT lifecycle:
- Do we have confidence in the ability of our team or the chosen solution to reliably provision, authenticate, configure, monitor, and update a growing number of devices over long periods of time?
- Does the solution support potential changes to our technology infrastructure in the future, such as different types of data and connectivity?
- Can we sustain the cost of truck rolls if this platform fails?
3. Application Integration
As shown in Figure 2, IoT solutions typically connect to a variety of enterprise infrastructure, services, and third-party software. Application integration therefore ensures that IoT data can flow transparently between devices and enterprise systems such as databases, reporting tools, and analytics platforms.
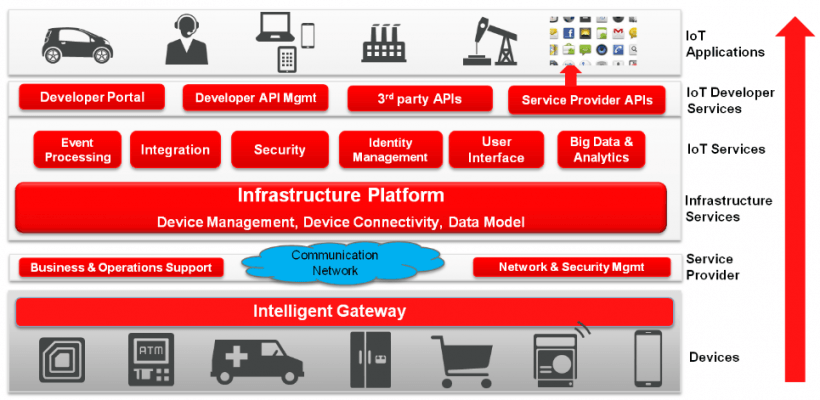
Robust APIs are needed to bridge the gap between endpoint devices, central monitoring and management dashboards, and other cloud applications and services or on-premises systems. These APIs must be extensible to avoid the software engineering time associated with integrating systems on a one-to-one basis.
While developing an API may seem trivial at first, there are many hidden challenges in creating a flexible API today that can also support the unforeseen requirements of tomorrow.
API testing alone, for example, consists of creating a manual or automated API testing process, continuously updating the data schema as API parameters change, testing parameter combinations, sequencing API calls, validating parameters, and repeatedly tracking system integration.
Such projects can redirect engineering resources from other core business operations, such as creating value-added features and services. To avoid this, organizations must ask themselves:
- Is the engineering cost of developing, testing, and managing an API that provides interoperability and data transparency budget well spent?
- Can we scale our resources to support this as the number and type of systems in our IoT solutions stack grows?
4. Security
Cyber attack vectors exist within the software, communications channels, firmware update processes, and physical components of an IoT solution.
Exacerbating the security challenge is the fact that IoT deployments typically consist of thousands of unique devices and users, with one security strategy that must address vulnerabilities for all of them. This security strategy must consider the edge node, network, and cloud, each of which has its own unique requirements and often must be tweaked to the requirements of a specific industry (Figure 3).
Not only can securing each of these tiers be expensive in its own right, the complexity of properly implementing security is extremely high. In light of this, decision-makers should question:
- Do we have enough high-quality security expertise on staff to secure all of the possible threat vectors in our device, network, and cloud systems?
- How prepared are we to respond if and when a security breach occurs?
- Can we afford the potential consequences of data loss/IP theft, reputational damage, or damage to property or people resulting from cyber threats?
The “Buy” Argument
Any “make versus buy” decision involves measuring how effectively internal development resources can handle setbacks over time against the more finite cost of partnering with domain experts. If the answer to any of the above questions is “no,” it is time to investigate partnership.
Partnering with domain and technology experts can help organizations focus on competencies and decrease time to market, while also allowing companies to scale more smoothly. After all, connectivity, device management, application integration, and security are all now fundamental components of any IoT deployment, and don't add much inherent value. A company's core expertise, on the other hand, does.
The Intel® IoT Solutions Alliance is an ecosystem of more than 150 members with proven track records of IoT partnership. Telit, for instance, brings more than 30 years of machine-to-machine communications experience to its IoT offerings, which span connectivity management, device management, application integration, and administration and security across a portfolio of edge networking modules and IoT platform solutions.
The Telit IoT Platform includes tools that address each of the areas outlined above, starting with Telit IoT Connectivity. Telit IoT Connectivity eliminates the complexity of managing multiple mobile network operators with global subscription services. It combines with the company's portfolio of LoRa and cellular communications modules to ease the burden of deploying IoT solutions across borders.
The Telit IoT Platform also provides device and data management features that enable remote configuration and updating in an ad hoc manner or using custom schedules. Devices can be segmented by parameters such as organization, location, or type so that specific system or user issues can be resolved or improved upon as efficiently as possible. According to Telit officials, roughly 80 percent of their back-end code is dedicated to system and device management.
Application integration is another of the Telit IoT Platform's strong suits, as it leverages the company's deviceWISE software framework to securely link IoT assets from edge node to enterprise. One of the strengths of deviceWISE is its compatibility with both brownfield and greenfield systems. This makes it particularly compelling in environments such as manufacturing where “rip and replace” strategies are not an option, and technologies must be integrated into IoT architectures (Figure 4). deviceWISE also includes connectors to enterprise applications and services such as Amazon, SAP, and IBM Watson so that organizations can quickly gather intelligence from their IoT infrastructure.
Security is baked into Telit solutions from their hardware connectivity modules through to their enterprise offerings. In fact, the Telit IoT Platform is in its third generation as the company continues to update its security infrastructure. It integrates encryption, SSL/TLS communication frameworks, session management, user permissions and access control, auditing, validation, and other security services.
IoT Decision Time: Fast Or Far?
Although engineers are inclined to build solutions on their own and fix issues as they arise, this approach is difficult in IoT deployments. With IoT rollouts expected to grow exponentially for the foreseeable future, organizations must be able to scale when the opportunity presents itself. Such opportunities will not wait for engineering roadblocks to be resolved.
An old proverb states: “If you want to go fast, go alone. If you want to go far, go together.” With technology partners that are able to close the loop on IoT infrastructure challenges, how far an organization can go is up to the innovation that lies within.
To learn more about “make versus buy” tradeoffs for IoT OEMs, watch the Telit webinar “The Importance of Partnerships, Flexibility, and Strategic Thinking When Designing and Implementing IoT Solutions.”